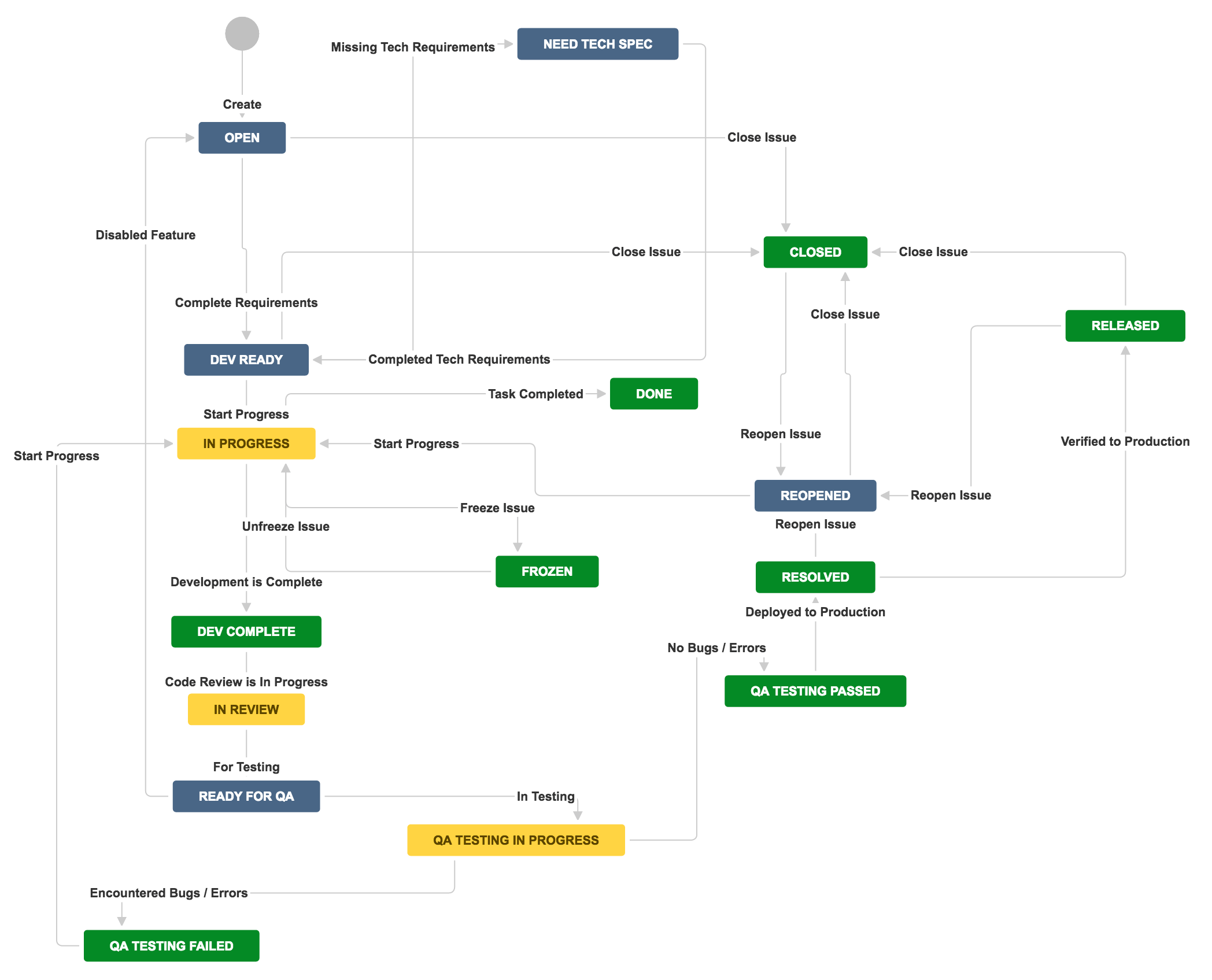
Exploring the Cutting-Edge: Connectivity and Infotainment Systems in Modern Vehicles
In today’s automotive landscape, the transformation from purely mechanical wonders to software-driven experiences has set an exhilarating pace for innovation and user engagement. As an auto enthusiast with a deep-rooted appreciation for the intersection of technology and automotive design, the evolution of connectivity and infotainment systems stands out as a pivotal element shaping our driving experiences. In this exploration, I aim to dissect the technical marvels behind modern infotainment systems, their impact on the driving experience, and the potential future developments in this space.
The Core of Modern Connectivity: Infotainment Systems
At the heart of modern vehicle connectivity lies the infotainment system. These sophisticated systems blend entertainment, information delivery, and user interface into a seamless cockpit experience. Through touchscreens, voice commands, and tactile buttons, drivers and passengers interact with a wide array of functionalities including navigation, media playback, and climate control, to name a few.
Technical Underpinnings
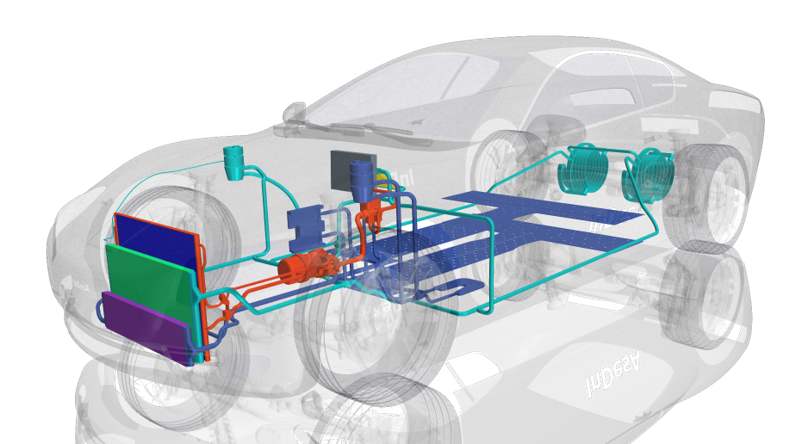
The technical scaffolding supporting these systems is built on a combination of hardware and software innovation. High-performance computing units serve as the brains, processing inputs and outputs at breakneck speeds to ensure responsiveness. Concurrently, sophisticated software platforms, often built on versions of Linux or Android, offer a customizable, scalable, and secure foundation for various applications and services.
Integration with smartphones via protocols like Apple CarPlay and Android Auto has exponentially increased the utility and appeal of these systems, mirroring our phones’ interfaces within the vehicle for a cohesive digital experience.
Challenges and Considerations
Yet, designing and implementing these systems is not without its challenges. Cybersecurity and user privacy emerge as primary concerns, demanding rigorous encryption and secure coding practices. Additionally, the quest for intuitive user interfaces necessitates the collaboration of user experience (UX) designers, cognitive psychologists, and software engineers to craft systems that are both powerful and accessible to users of all tech proficiencies.
< >
>
Impact on the Driving Experience
The proliferation of connectivity and infotainment systems has profoundly altered how we interact with our vehicles. Navigation systems with real-time traffic updates have recalibrated our expectations for travel efficiency. Streaming services ensure our favorite podcasts and playlists are always within reach, transforming even mundane commutes into enjoyable experiences. Furthermore, these systems enhance safety through features like hands-free calling and voice-controlled operations, minimizing distractions.
Envisioning the Future of Vehicle Connectivity
Looking ahead, the horizon of connectivity and infotainment systems brims with potential. Advancements in Artificial Intelligence (AI) and Machine Learning (ML) promise more personalized and anticipatory user experiences, adapting to our preferences and habits. The integration of augmented reality (AR) into windshield displays could redefine navigation, overlaying directional arrows directly onto the road ahead.
Furthermore, as vehicles become more connected to the urban fabric through the Internet of Things (IoT), infotainment systems could serve as hubs for not only vehicle-centric services but also for interacting with smart city infrastructures, offering truly integrated mobility solutions.
In conclusion, the evolution of connectivity and infotainment systems is set to redefine the automotive experience continually. As an enthusiast who has navigated the evolution of automotive technologies, I am especially excited about these developments. Their potential to enhance safety, efficiency, and enjoyment on the road holds the promise of not just a new era of driving but a new paradigm of mobility.
< >
>
Driven by my experiences as both a technologist and an auto enthusiast, I view the advancement of these systems as an exhilarating challenge — one where the journey is as rewarding as the destination. As we steer towards this future, the relationship between driver, vehicle, and technology will undoubtedly become more intertwined, crafting experiences that were once the realm of science fiction.
< >
>
The journey towards this future is something I engage with both professionally, through my consulting work at DBGM Consulting, Inc., and personally, as an avid follower and contributor to the sphere of automotive innovations. The path forward is rich with opportunities for enhancing connectivity and crafting infotainment systems that enrich our lives in motion, making every journey an experience in its own right.
 >
> >
> >
> >
> >
> >
> >
> >
> >
>





 >
> >
> >
>