Advanced Smartphone Projects: Leveraging Android Application Development for Innovative Solutions
With over five hundred smartphones in my collection, I have completed hundreds of projects centered around Android, Windows Mobile, and iOS, utilizing technologies such as Kotlin and Java for Android application development. Before smartphones became widespread, I worked on numerous projects involving flip phones, PDAs, etc.
Each phone in my collection is part of a unique project ranging from acting as a Bluetooth File server or remote IP camera to serving as a full PHP/SQL/FTP/DHCP server or being the platform for the development of a custom ROM. At the very least, each phone is rooted and has a ROM I modified for that model specifically flashed to it. In the case a phone can’t be rooted (ZTE has a couple that come to mind), I usually find these phones make great security studies. The ZTE phones, for instance, have a security measure similar to Deep Freeze by storing system critical files in a mounted and temporary RAM drive, leaving the real files always encrypted and hidden.
Some of the major projects include Custom ROM builds, Rooting Techniques, and Client/Server Projects. For example, the Custom ROM builds involve major system alterations to the Android build that require rooting, partition resizing and flashing, init.d and kernel modifications, service modifications, apk decompile and recompile events, and more. Some of the devices where custom ROM builds were implemented include Motorola Nexus 6 MRA58K Marshmallow, LG Nexus 4 MY48M Lollipop, and Samsung Galaxy S2 GT-I9100 SprintROM.
In addition, my experience in Android application development allowed me to create client/server projects such as DHCP, UPnP, DNS, Email (POP3 / SMTP), FTP Proxy, FTP, FTPS, FTPES, Load Balancer, MySQL, NFS, PHP, PXE, Port Forwarder, RTMP, Remote Control, SMB/CIFS, SFTP, SSH, TFTP, Telnet, Time, Torrent Client, Torrent Tracker, VNC, VPN, Wake On Lan, Web, and X11. Some of these projects involve web hosting on Android, such as hosting PHP, SQL, and JavaScript on Android devices.
My expertise in Android application development using Kotlin and Java has been invaluable in successfully completing these projects.
Custom ROM builds
These examples involves major system alterations to the Android build that require rooting, partition resizing and flashing, init.d and kernel modifications, service modifications, apk decompile and recompile events, etc.
- Motorola Nexus 6 MRA58K Marshmallow
- LG Nexus 4 MY48M Lollipop
- Amazon Kindle Fire HD (converted to Google Play Device)
- Samsung Galaxy S2 GT-I9100 SprintROM
- Samsung Galaxy S3 JZO54K Jelly Bean
- Samsung Galaxy Ace s765c Build
- LG Volt LS720 KOT491 KitKat
- LG Optimus Zone 3 VS425PP Lollipop
- LG Optimus Zone 2 VS415PP
- LG Optimus Zone 1 VS410PP
- LG Tribute LS660 KVT49I
- LG Tribute 2 LS665 LMY47V
- LG Lucky LGL16CB Build
- LG Sunrise LGL15C Build (Same as Lucky, but GSM)
- LG Sunset LGL33L Build
- Pantech Breakout S8995VWCA55F.BB
- ZTE Paragon Z753G Build
- ZTE Speed ZTE9130ABB
- AND MANY MANY MORE!
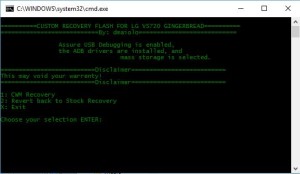
For example, here is the structure for a custom ROM built for the LG Esteem. In this example, this is deployed in CWM Recovery once the phone is rooted as shown further below.
.android_secure.vfat.tar -- Move2SD Platform 100% Custom boot.img -- Stock LG Boot Partition cache.yaffs2.img -- Cache With Modifications for /SDCard Mounting data.yaffs2.img -- Data Partition 100% Custom nandroid.md5 -- Md5 Checksum recovery.img -- CWM Recovery by ClockworkMod system.yaffs2.img -- LG Stock System Partition with Heavy Modifications (40% Custom)
Rooting Techniques
Rooting can be challenging for some, but as rooting methods have become easier to implement using ADB Debug tools, I always try to look for more challenging root methods. In my collection I have:
- Successfully rooted over 250 Android smartphones
- Jailbroken over 50 iOS smartphones
- Developed new rooting methods based on prior developers work
- Temp rooted three ZTE models that have never been rooted before
Here I modify an LG Esteem Root script by Dan Rosenberg (@djrbliss) to allow for automatic root flashing…
echo Waiting for device...
adb kill-server
adb wait-for-device
echo Push Zergrush...
adb push zergrush /data/local/tmp/zergrush
adb shell "chmod 755 /data/local/tmp/zergrush"
adb shell "echo exit | /data/local/tmp/zergrush"
echo Install Root Tools...
adb shell /data/local/tmp/sh -c "mount -orw,remount /dev/block/system /system"
adb shell /data/local/tmp/sh -c "mkdir /system/tmp"
adb shell /data/local/tmp/sh -c "chmod 777 /system/tmp"
adb push su /system/tmp/su
adb push busybox /system/tmp/busybox
adb push Superuser.apk /system/tmp/Superuser.apk
echo Installing flash_image...
adb push flash_image system/tmp/flash_image
adb shell /data/local/tmp/sh -c "mv /system/tmp/flash_image /system/xbin/flash_image"
adb shell /data/local/tmp/sh -c "chmod 777 /system/xbin/flash_image"
echo Installing recovery.img...
adb push recovery.img system/tmp/recovery.img
adb shell /data/local/tmp/sh -c "mv /system/tmp/recovery.img /system/xbin/recovery.img"
echo Installing super user...
adb shell /data/local/tmp/sh -c "mv /system/tmp/su /system/xbin/su"
adb shell /data/local/tmp/sh -c "mv /system/tmp/Superuser.apk /system/app/Superuser.apk"
adb shell /data/local/tmp/sh -c "mv /system/tmp/busybox /system/xbin/busybox"
adb shell /data/local/tmp/sh -c "chown root /system/xbin/su"
adb shell /data/local/tmp/sh -c "chmod 4755 /system/xbin/su"
adb shell /data/local/tmp/sh -c "ln -s /system/xbin/su /system/bin/su"
echo Installing busybox...
adb shell /data/local/tmp/sh -c "chmod 755 /system/xbin/busybox"
adb shell /data/local/tmp/sh -c "/system/xbin/busybox --install /system/xbin/"
echo Flashing Recovery to CWM...
adb shell /data/local/tmp/sh -c "/system/xbin/flash_image recovery /system/xbin/recovery.img"
echo Cleaning up...
adb shell /data/local/tmp/sh -c "rmdir /system/tmp"
adb shell /data/local/tmp/sh -c "rm /system/xbin/recovery.img"
adb shell "rm /data/local/tmp/* 2>/dev/null"
echo Rebooting into CWM recovery...
adb reboot recoveryFaraday Cages: Antenna and Chipset Shielding
Communication with vendors and manufactures is a key security requirement on many handsets. By utilizing shielding techniques, I have been able to bypass security measures including:
- Block Verizon application expiration checking on Samsung Gusto 2 and 3 flip phones
- Bypass Verizon service checks to allow data and voice on unactivated phones
- Downgrade LG and ZTE mandatory security patches
* I have always worked with my collection as a personal challenge, and do not sell or distribute any techniques that comprise the security of a manufacturer or cellular provider, so please don’t ask
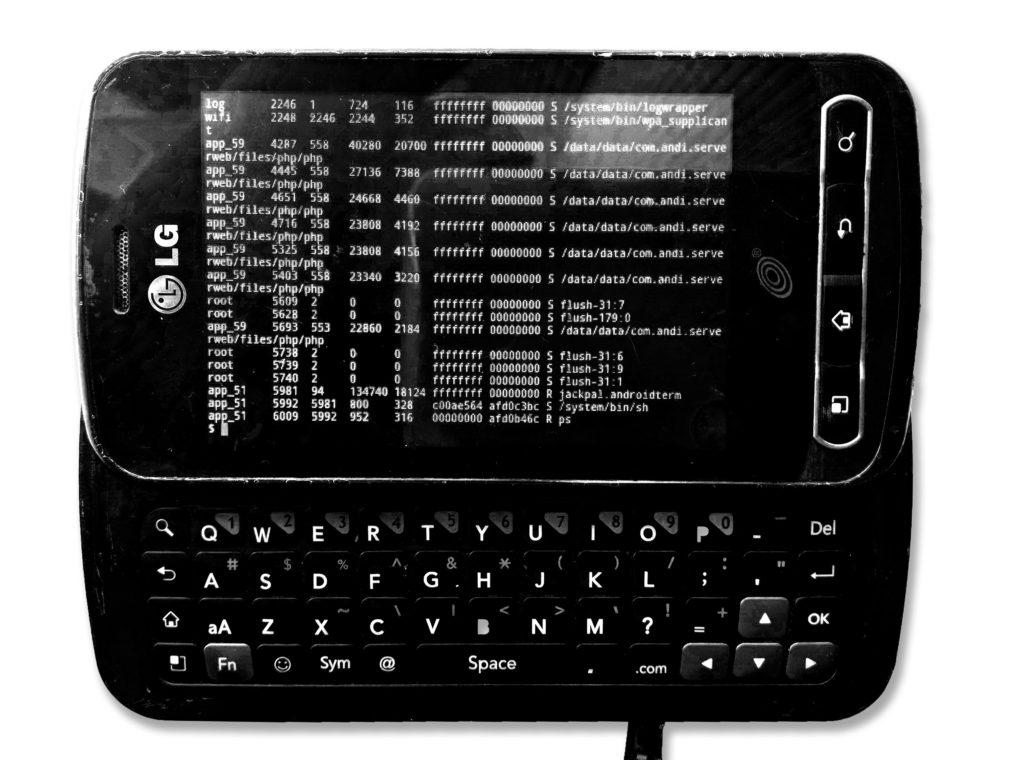
Client / Server Projects
The tiny chips carried inside our smartphones carry a wealth of untapped power. Throughout the years I have turned these little devices into all sorts of servers, including:
DHCP, UPnP, DNS, Email (POP3 / SMTP), FTP Proxy, FTP, FTPS, FTPES, Load Balancer, MySQL, NFS, PHP, PXE, Port Forwarder, RTMP, Remote Control, SMB/CIFS, SFTP, SSH, TFTP, Telnet, Time, Torrent Client, Torrent Tracker, VNC, VPN, Wake On Lan, Web, X11!
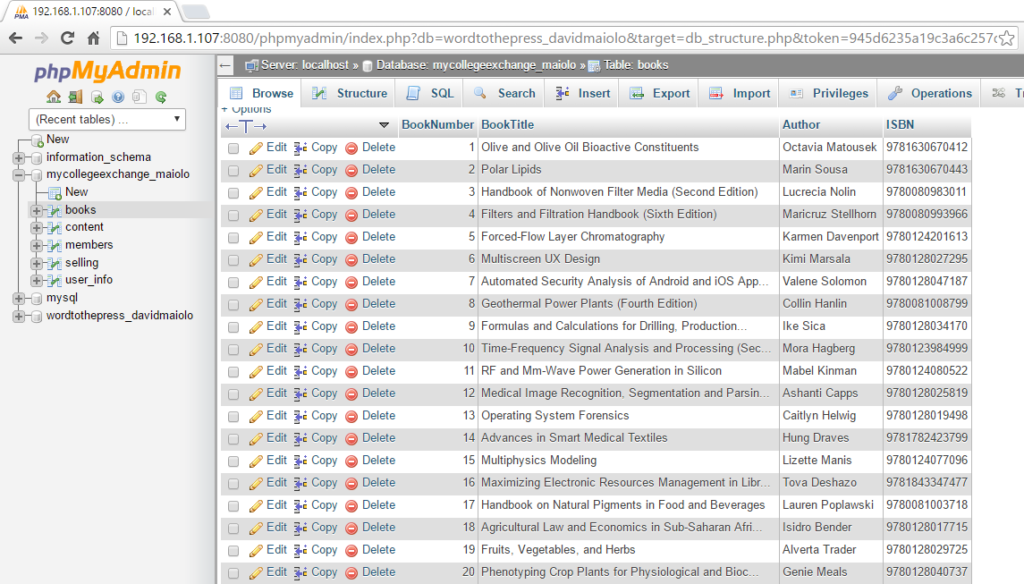
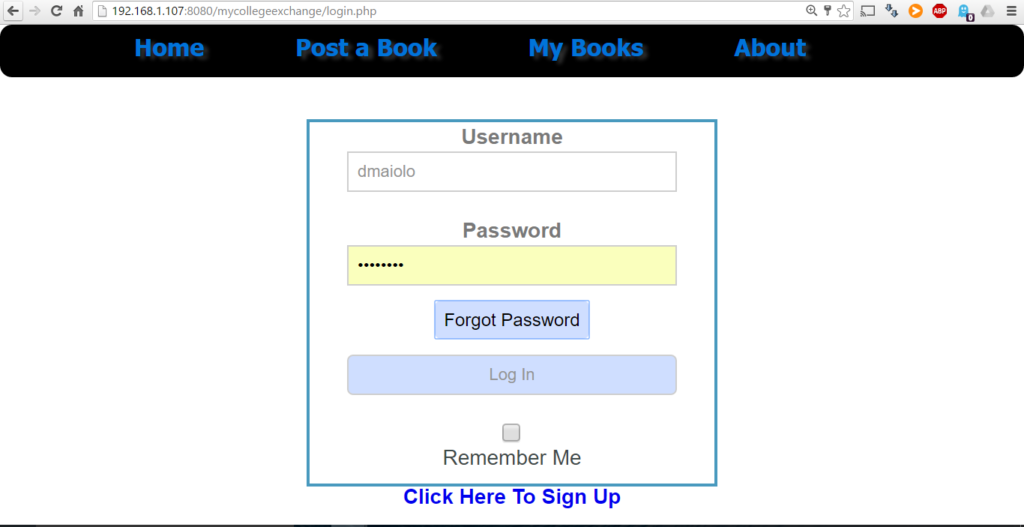
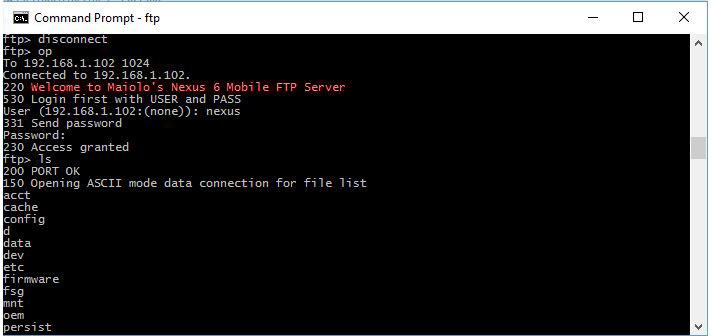
FTP/PHP/SQL/JavaScript Web Hosting On Android
For a time, this very portfolio website was hosted on a single smartphone! Here are some instances of different projects involving servers hosted on Android devices.
Here are some random IC shots from various projects:







Leave a Reply
Want to join the discussion?Feel free to contribute!