Active Directory: Troubleshooting & Overview
This tutorial provides an overview of Active Directory (AD), which is a collection of services used to manage identity and access for and to resources on a network. The tutorial describes various AD services, such as Domain Services, Lightweight Directory Services, Certificate Services, Federation Services, Rights Management Services, and Flexible Single-Master Operations (FSMO) Roles, including their functions, requirements, and usage. The tutorial also covers the Kerberos authentication method used in AD and provides tips and tools for diagnosing and troubleshooting common AD issues. The author created this tutorial to help others gain a better understanding of AD and to prepare for diagnosing AD issues in preparation for a Microsoft interview.
Active Directory Overview
I created this guide to assist in the general understanding of Active Directory and to give some examples of diagnosis procedures. Active directory is a collection of services (Server Roles and Features) that are used to manage identity and access for and to resources on a network. Initially, Active Directory was only in charge of centralized domain management. Starting with Windows Server 2008, however, Active Directory became an umbrella title for a broad range of directory-based identity-related services.
Active Directory Services
Domain Services
Active Directory Domain Services (AD DS) is central of every Windows domain network. It stores data about users and computers on the domain, verifies their credentials and defines their access rights. The server (or the cluster of servers) running AD DS is called a domain controller. A domain controller is contacted when a user logs into a computer or accesses another computer across the network.
*Other AD services, as well as many Microsoft server technologies rely on or use Domain Services; examples: Group Policy, Encrypting File System, BitLocker, Domain Name Services, Remote Desktop Services, Exchange Server and SharePoint Server.
Lightweight Directory Services
Active Directory Lightweight Directory Services (AD LDS) is a light-weight implementation of AD DS. AD LDS runs as a service on Windows Server. AD LDS shares the code base with AD DS and provides the same functionality, including an identical API, but does not require the creation of domains or domain controllers.
Certificate Services
Active Directory Certificate Services (AD CS) establishes an on-premises public key infrastructure (PKI). It can create, validate and revoke public key certificates for uses of an organization. These certificates can be used to encrypt files (when used with Encrypting File System), emails, and network traffic (VPNs, IPSec, etc.).
*AD CS requires an AD DS infrastructure
Federation Services
Active Directory Federation Services (AD FS) is a single sign-on service. With an AD FS infrastructure in place, users may use several web-based services (e.g. internet forum, blog, online shopping, webmail) or network resources using only one set of credentials stored at a central location, as opposed to having to be granted a dedicated set of credentials for each service. AD FS’s purpose is an extension of that of AD DS: The latter enables users to authenticate with and use the devices that are part of the same network, using one set of credentials. The former enables them to use the same set of credentials in a different network.
*AD FS requires an AD DS infrastructure, although its federation partner may not.
Rights Management Services
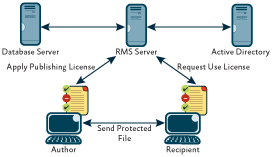
Active Directory Rights Management Services (AD RMS, known as Rights Management Services or RMS before Windows Server 2008) is used for information rights management. It uses encryption and a form of selective functionality denial for limiting access to documents such as e-mails, Word documents, and websites, and the operations authorized users can perform on them.
Flexible Single-Master Operations (FMSO) Roles
These are also known as the Operation Master Roles.
- Some operations can only be performed on one server (for instance, the DC)
- However other roles can be split to an individual server to guarantee operations to it will be consistent.
- It also eliminates replication conflicts.
- Roles can be moved from DC to DC
- Certain AD functions require these roles and will fail if the role/server is down.
- Roles are Forest Wide or Domain Wide
Forest-Wide Roles
Schema Master (One per forest)
- Defines the design of AD database
- Some software, such as Exchange, will expand the Schema
- Once the schema is expanded, you can’t go back.
- Not available? You can’t expand the schema
- This role is not used very often, so Microsoft recommends keeping with Domain Naming Master role on same server, tucked away.
Domain Naming Master (One per forest)
- Used when adding/removing domains from the forest
- Ensures two domains are not added with the same name.
- Not available? You can’t add/remove any domains within then forest.
- This role is not used very often, so Microsoft recommends keeping with Schema Master role on same server, tucked away.
Forest DNS Zone Master role (one per forest)
- Responsible for coordinating the adding or deleting of the forest-wide records on the DNS servers that host the top-level DNS zone.
- These records contain the names of the Global Catalog (GC) servers.
Domain-Wide Roles
PDC (Primary Domain Controller) Emulator (One per domain)
- Originally in place to make bridge between Win2000 DC and NT4 DC
- Generally, not used if you don’t use any NT domain controllers, but still provides:
- Keeps time accurate in the domain (other DCs will sync time with PDC)
- Finally authority on passwords – password changes are sent to PDC with urgent replication (it has the most up to date password changes so a DC can contact PDC if password given is wrong to assure its really wrong)
- DFS changes are made on PDC emulator
- Group policy editing defaults to the PDC
RID (Relative Identifier) Master (One per domain)
- Allocates RID Pools
- RID’s appended to end of SID’s (Security Identifier)
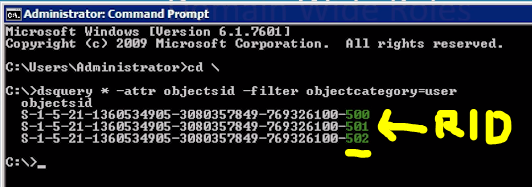
- Not available? OK for a little while as DC asks for them before they run out. But, if down for too long, no new AD objects can be created.
Infrastructure Master (One per domain)
- Keeps object references consistent across domains in the forest
- Updates multi domain references
- With a multi domain forest
- Make sure all DC’s in forest are Global Catalog servers
Domain DNS Zone Master role (one per domain)
- Responsible for coordinating the adding or deleting of any AD-integrated DNS zones on the DCs with DNS servers that host the domain.
Global Catalog (GC) Server
Each domain has its own copy of the AD database. This is stored in the NTDS.DIT (THE Active Directory database file) and changes are replicated to each DC in the domain. This is fine if you want to access resources in the same part of the domain, however is a problem if you want to access resources in a different part of the forest.
In a multi-domain forest, if you want to access a resource, and don’t know where it is, this can be a problem. Therefor a Global Catalog server acts as an index for the entire forest. The GC only contains a subset of each objects attributes (just enough to be searchable). This allows users in a domain to run queries against the GC to find any objects in the forest.
GC Facts
- Any Domain Controller can be a GC
- Must have one per domain (should have more than one for redundancy)
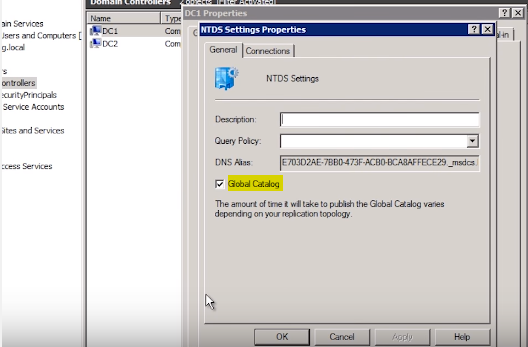
Turn on/off GC
Turn on/off the Global Catalog in the NTDS (NT Directory Services) settings within Active Directory Users and Computers -> Domain Controllers.
Reasons to Deploy a GC
- Can only see what users are in a Universal Group (used to assign permissions to related resources in multiple domains) with a GC
- GCs are required when logging in with a Universal Principal Name (UPN) – username@domain
- Used to locate directory information regardless of where user is in the forest
- Need to be at sites connected by a WAN link (perhaps DC is blocked by firewall)
- Software, such as Exchange, requires a GC
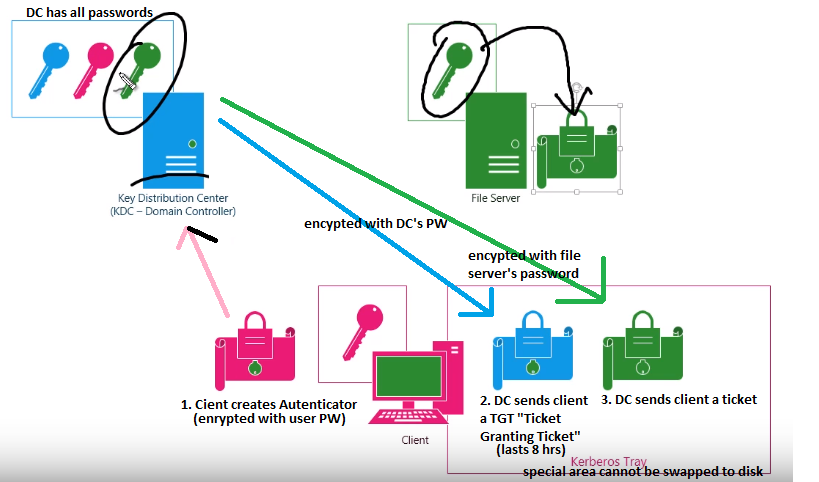
Kerberos in AD
Kerberos is the native authentication method in Active Directory, so it’s used by Windows Networks everywhere.
- A client creates an Authenticator that is encrypted with the users password and sends to the KDC
- The KDC checks if the password is correct, and if so, returns a Ticket Granting Ticket TGT encrypted with a key only KDC knows
- Client sends the Ticket Granting Ticket TGT back to the KDC with a request to access the file server.
- If KDC trusts its own password in the TGT, it knows it generated the TGT and sends client back a Ticket encrypted with the file server’s logon password
- Now, for the next 8 hours, the client sends a copy of the ticket to the file server and if it can decrypt the ticket, it knows the KDC generated it, so its legit.
- File server will use ticket (which also has clients username, etc) to decide what user can access.
Overview of Kerberos Process
How to View Kerberos Tray
Use klist.exe to view the Kerberos tray.
klist tickets
Use klist.exe to view the Kerberos sessions.
klist sessions
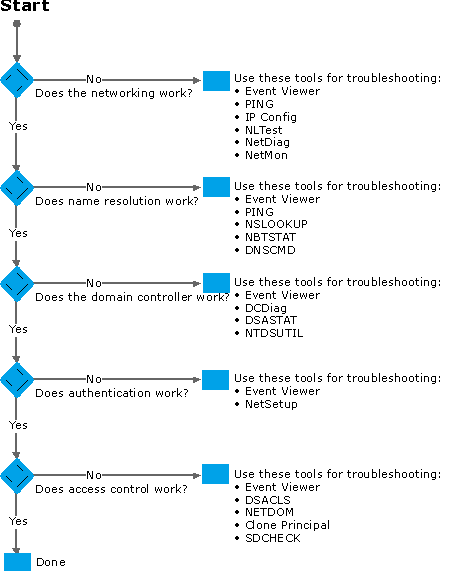
AD Troubleshooting Tools
This flow-chart will provide an overview of steps you can utilize to diagnose Active Directory. Information from chart derived from Microsoft.
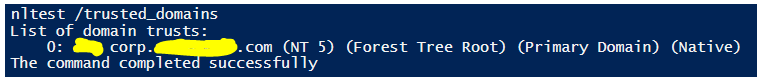
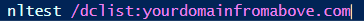
Use NLTest to show trust relationship
Ntlest /trusted_domains
Nltest /dclist:yourdomain
AD replication troubleshooting
When looking at Active Directory replication, you may notice an update or updates have not arrived/replication. This could be caused by DNS problems, networking problems, or security issues.
Get a List of the Replication Errors Encountered
To get a list of the replication errors, and export them to a CSV file, run the following command
repadmin /showrepl * /csv > replication_errors.csv
Use this to resolve replication failures. Sort by latest and hide unneeded columns.



Leave a Reply
Want to join the discussion?Feel free to contribute!