SCCM / WSUS Software Update Best Practices
Overview
This article contains a recommended set of procedures and schedules you can follow in your environment to obtain great WSUS compliance within SCCM. I developed these best practices and helped a client implement them to improve their compliance.
Schedule
I recommend that you create a schedule in your environment to check/complete the following WSUS components/tasks.
|
Weekly |
|
All Software Update Cleanup of Superseded and Expired |
|
Software Update Groups Cleanup |
|
Monthly |
|
Set MaxExecutionTime on Specific SCCM Software Updates |
|
Cleanup Packages from DPs that are not Needed at DPs |
|
Remediate Updates that are required but not deployed |
|
Notification of Network Segment Creation |
|
Quarterly |
|
Verify Packages and Applications are NOT Updated to DPs on a Schedule |
|
Manage SCCM Deployment Threads |
|
Manage SCCM Distribution Point Rate Limits (Time-Slice Based Throttling) |
|
Manage SCCM Distribution Point Priority Schedules |
|
Enable Binary Differential Replication on Deployment Packages |
|
Project Based |
|
Maximize Performance and Coverage of Automatic Deployment Rules |
|
Allow Site Server and Microsoft to be used as fallback Update locations for Updates |
Network Segment Creation
Overview
When a new network segment is created within your environment, be sure the new segment is communicated.
Procedure
- Work with your Network engineers to be included in communication when new network segments are created.
Set MaxExecutionTime on Specific SCCM Software Updates
Overview
Every update in SCCM has a maximum amount of time that it is allowed to run. If the amount of time it takes to install the update exceeds the MaxExecutionTime variable set for the update, the update will fail to install. Increasing this execution time can allow a greater installation success rate.
Procedure
-
Run from NNN(Your SCCM Sever): Powershell:
Get-CMSoftwareUpdate -name "*Cumulative Update*" -Fast | ? {$_.MaxExecutionTime -lt '1800'} | Set-CMSoftwareUpdate -MaximumExecutionMins 30 Get-CMSoftwareUpdate -name "*Cumulative Security Update*" -Fast | ? {$_.MaxExecutionTime -lt '1800'} | Set-CMSoftwareUpdate -MaximumExecutionMins 30 Get-CMSoftwareUpdate -name "*Security Monthly Quality Rollup*" -Fast | ? {$_.MaxExecutionTime -lt '1800'} | Set-CMSoftwareUpdate -MaximumExecutionMins 60 Get-CMSoftwareUpdate -name "*Security and Quality Rollup*" -Fast | ? {$_.MaxExecutionTime -lt '1800'} | Set-CMSoftwareUpdate -MaximumExecutionMins 30Examples
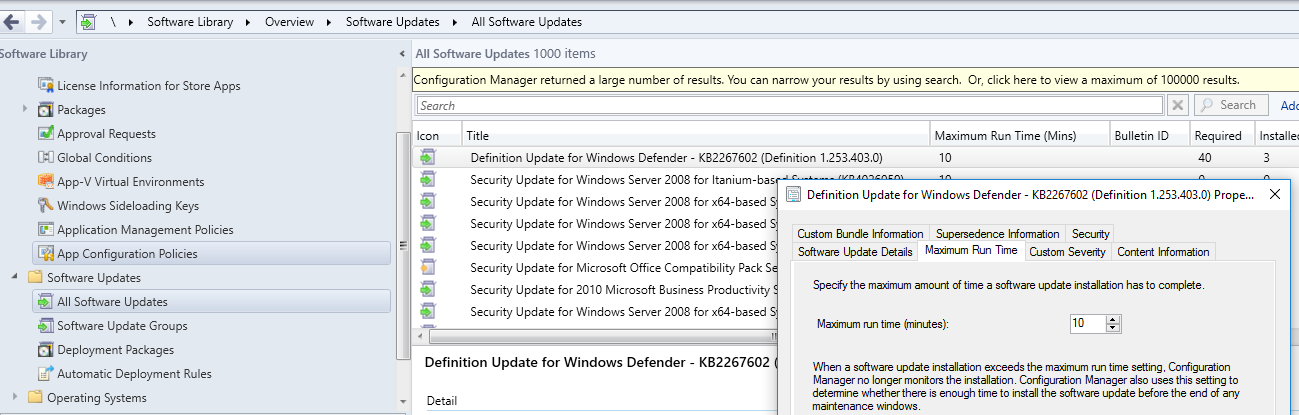
Figure 1 Maximum Run Time on a Software Update
Cleanup Packages from DPs That are Not Needed
Overview
Overtime, SCCM Distribution Points out will accumulate updates and applications that are no longer applicable to the particular DP. For example, if an older version of Adobe Reader were needed in 2015, leaving the installation files on the DP is using unnecessary space.
Procedure
-
View Active Deployments
- Within the SCCM Console, open Monitoring\Overview\Deployments
- Sort by Date Created
-
Cross Reference Active Deployments with DP Content, And Remove Unneeded
- Administration\Overview\Distribution Point Groups -> Branch Distribution Groups [Right Click -> Properties]
- Content Tab -> Click Unneeded Updates -> Remove
Examples
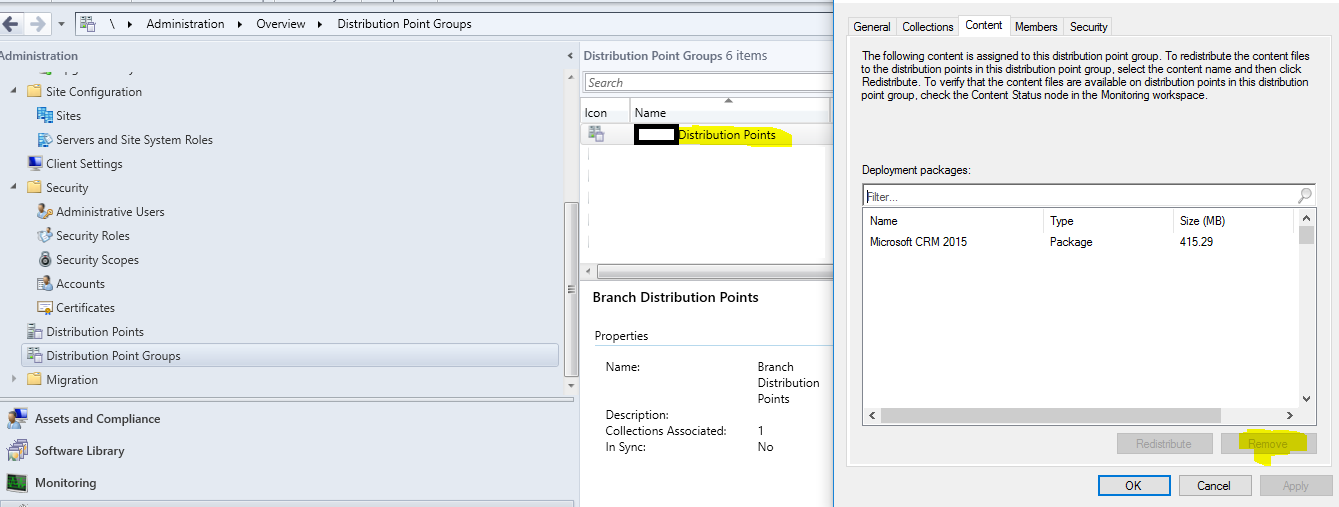
Figure 2 Removing DP Content
Verify That Applications are NOT Updated to DPs on a Schedule
Overview
Within the SCCM Console there is an option to have content automatically redistribute itself to distribution points on a schedule. When found to be enabled on content, the processes unnecessarily consumes SCCM traffic.
Procedure
- Open a suspected offending application or package
-
For example, open Software Library\Overview\Application Management\Packages\Workstations\
System Configurations\NCI - [Right Click] Properties -> Data Source -> Update Distribution points on a schedule
- Verify this is unchecked
Examples
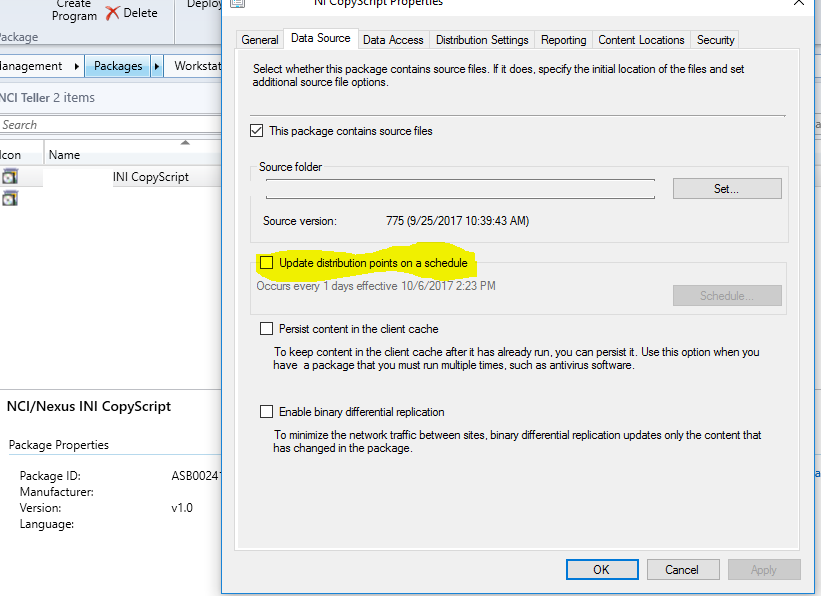
Figure 3 Verifying content is not updated on schedule
Manage SCCM Deployment Threads
Overview
SCCM controls the number of packages it will attempt to distribute at one time, and the number of distribution points it will attempt to distribute the packages to. Adjusting these controls will allow maximum throughput of traffic while maintaining throttling constraints.
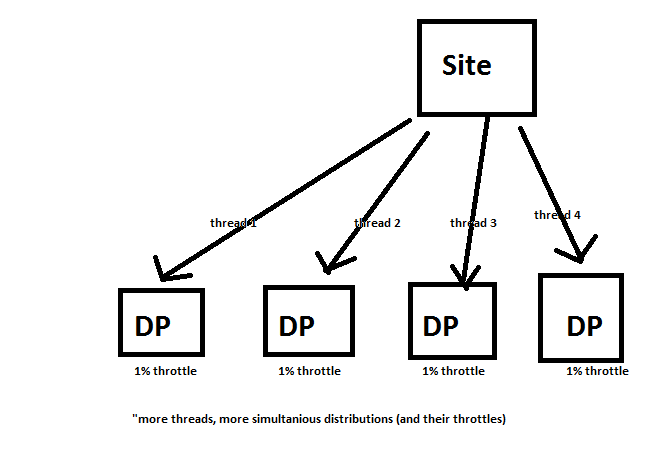
Figure 4 SCCM Content Threads
Procedure
- Within the SCCM Console go to Administration\Overview\Site Configuration\Sites\XXX
- [Right Click] Configure Site Components -> Software Distribution
- Adjust Maximum Threads
Monitoring Threads
- Download and Install the System Center 2012 R2 Configuration Manager Toolkit
- Open the DP Job Manager Tool at C:\Program Files (x86)\ConfigMgr 2012 Toolkit R2\ServerTools\DPJobMgr.exe
- Use the Manage Jobs tab to monitor
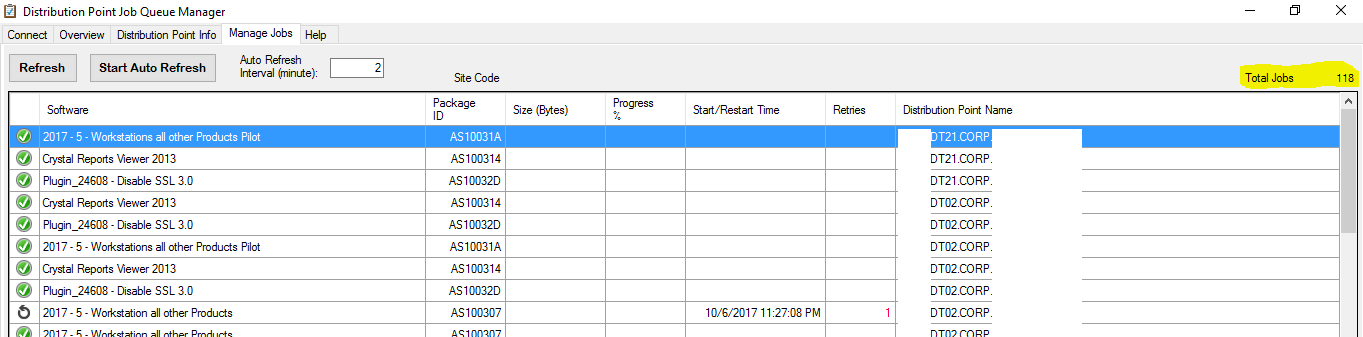
Figure 5 DP Job Manager Tool
Examples
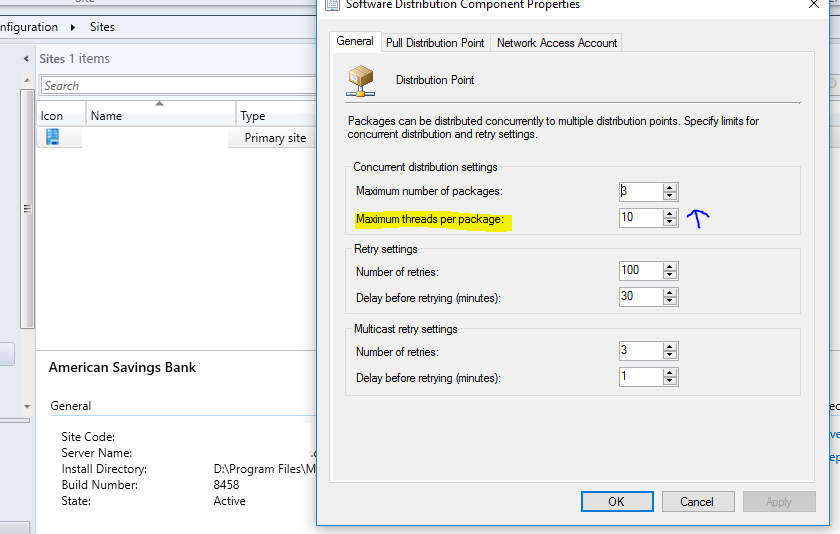
Figure 6 Adjusting Content Threads
Manage DP Rate Limits (Time-Sliced Throttling)
Overview
Distribution Point Rate limits are a form throttling which applies to content distribution. Adjusting these throttles can help maximize performance while minimizing disruption during the workweek.
Procedure
- Within the SCCM Console go to Administration\Overview\Distribution Points [Right Click DP] Properties
- Open the Rate Limits tab
- Adjust accordingly
Examples
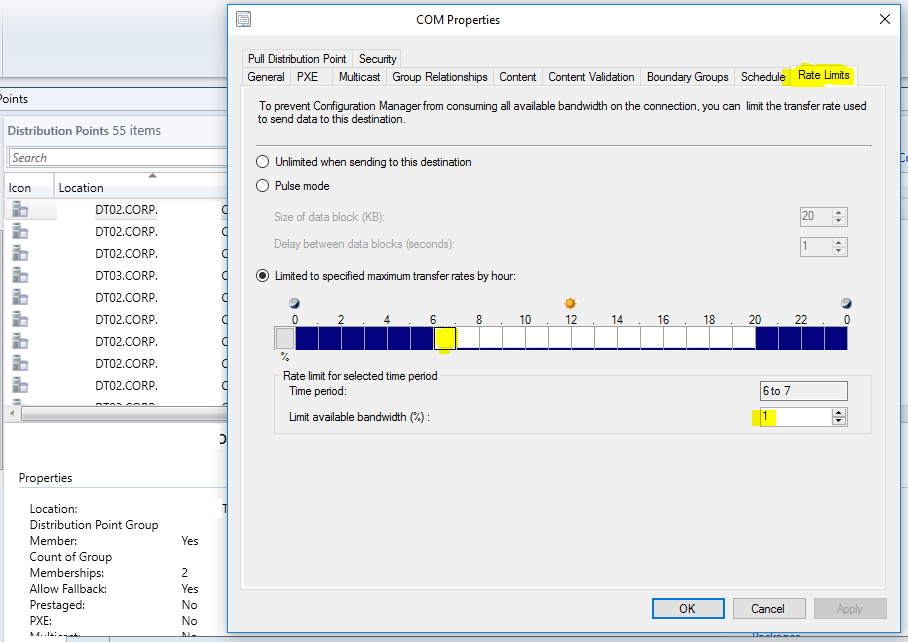
Figure 7 Adjusting DP Rate Limits
Manage SCCM Distribution Point Priority Schedules
Overview
Distribution schedules allow low, medium and high priority deployments to adhere to certain schedules. Adjusting these schedules can help maximize performance while minimizing disruption during the workweek.
Procedure
- Within the SCCM Console go to Administration\Overview\Distribution Points [Right Click DP] Properties
- Open the Schedule tab
- Adjust accordingly
Examples
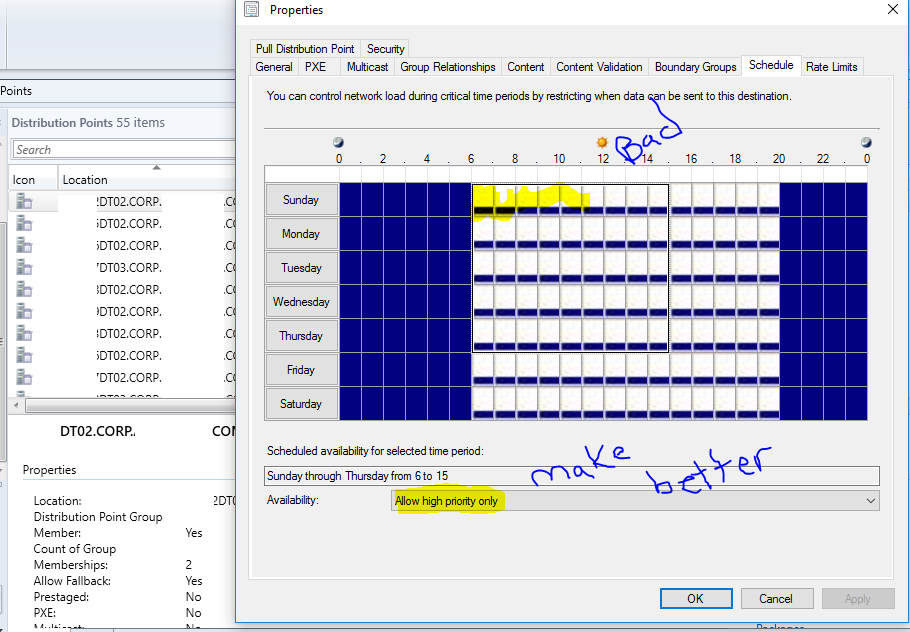
Figure 8 Adjusting DP Priority Schedules
Maximize Performance and Coverage of Automatic Deployment Rules
Overview
When creating SCCM ADRs, it is important that no rule duplicates another, and also that combined rules do not miss any critical or security updates for an environment (such as Prod or Pilot)
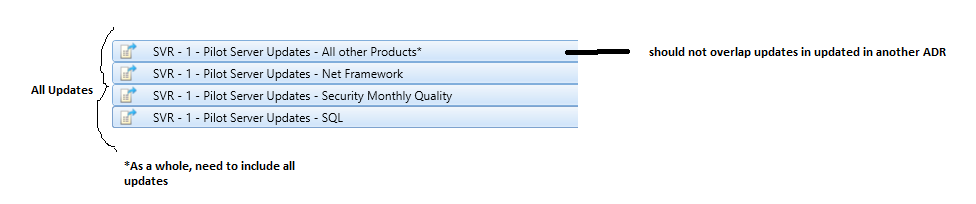
Figure 9 Optimizing ADRs in SCCM
How Microsoft Deploys Software Updates
Security Only Quality Update (Released every month)
- Includes Critical and Security for That Month
Security Monthly Quality Rollup (Released every month)
-
Includes Critical, Security and Updates*, Cumulative for Year
* Feature patches (non-security)
Procedure
- Within the SCCM Console go to Software Library\Overview\Software Updates\Automatic Deployment Rules
- A Deployment Packages are updated via an ADR no more frequently than necessary. For example, a pilot ADR may update weekly, whereas a Production ADR may update monthly.
Enable Binary Differential Replication on Deployment Packages
Overview
Binary Differential Replication, sometimes known as “delta replication,” is used by SCCM to update package source files with a minimum of additional network traffic. This minimizes the network traffic between sites, especially when the package is large and the changes are relatively small.
Procedure
- Within the SCCM Console go to Software Library\Overview\Software Updates\Deployment Packages
- [Right Click Package] and check Enable binary differential replication
Examples
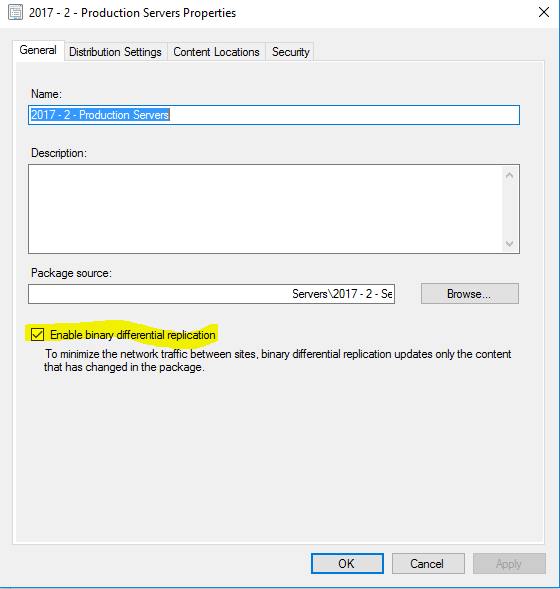
Figure 10 Enabling Binary Differential Replication
Allow Site Server and Microsoft to be used as Fallback Update Locations
Overview
If there is no distribution point assigned to a client, updates can fail to deploy. Allowing a fallback source to be used, which increases the chances your clients will receive their required updates.
Procedure
- Within the SCCM Console go to Software Library\Overview\Software Updates\Automatic Deployment Rules
- Click an ADR, and then go to the Deployment Settings tab at the bottom of the screen
- [Right Click] Properties
- Open the Download Settings tab and check If software updates are not available…
Examples
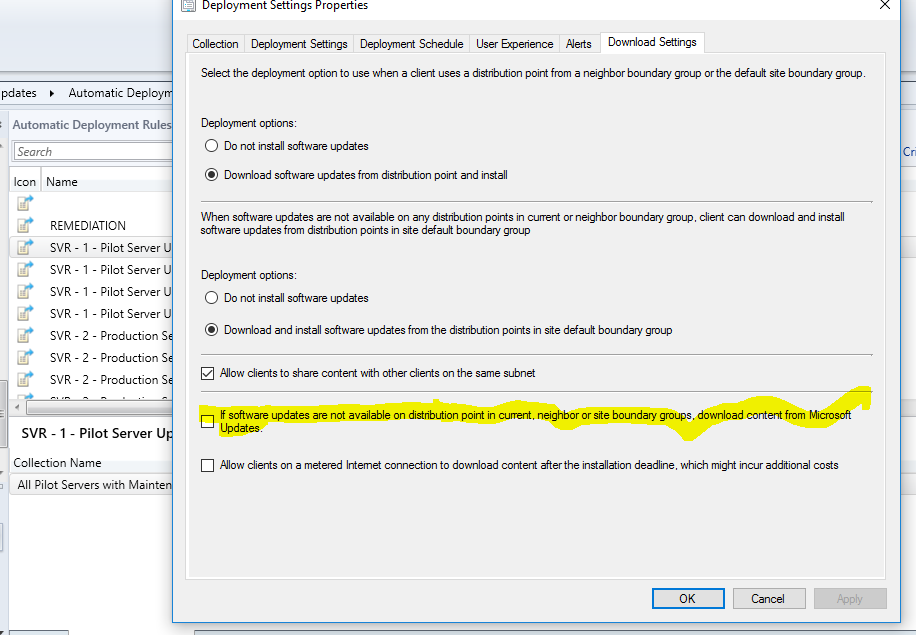
Figure 11 Configuring Failback Sources for ADRs
Remediate Updates That Are required but not deployed
Overview
There is a prebuilt SCCM report that can help identify updates that are required, but have not been distributed. I have further configured the ability automate this portion in a different project. Please see SCCM: Automate Deployment of Required Updates for more details.
Procedure
- Using Internet Explorer, browse to the Reports path at http://vconscm005prd/Reports
- Find the report Management 2 – Updates required but not deployed and run it
- Collection: ‘Production Workstation’ and ‘Production Server’ (one report for each)
- Vendor: Microsoft
- Update Class: Critical and Security (one report for each)
- Export each report as updates_nn.csv
-
Connect to NNN: PowerShell console and use the report to update Software Update Groups accordingly:
$updates =import-csv -path updates_nn.csv $undeployedupdates=$updates | %{Get-CMSoftwareUpdate -ArticleId $_.update -Fast | ?{$_.nummissing -ge 1}} $PilotSoftwareUpdategroup=Get-CMSoftwareUpdateGroup -Name "Production Servers Updates - All other Products* nnn" $undeployedupdates | %{Add-CMSoftwareUpdateToGroup -SoftwareUpdateId $_.CI_ID -SoftwareUpdateGroupName "Production Servers Updates - All other Products* nnn"}Examples
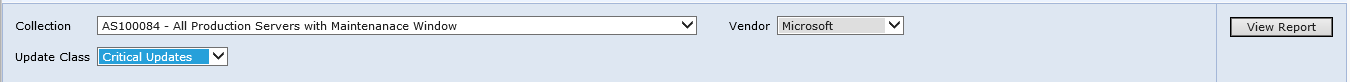
Figure 12 Checking Critical Updates
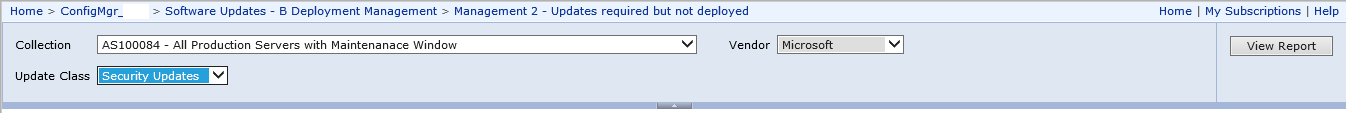
Figure 13 Checking Security Updates
Software Update Cleanup of Superseded and Expired
Overview
Superseded and Expired updates need to periodically be cleaned up from Software Update Groups.
Superseded Updates Procedure
- Within the SCCM Console go to Software Library\Overview\Software Updates\All Software Updates
- Add Criteria -> Superseded + Deployed
- [Right Click] Edit Membership -> Uncheck from each Deployment Package
Expired Procedure
- Within the SCCM Console go to Software Library\Overview\Software Updates\All Software Updates
- Add Criteria -> Expired + Deployed
- [Right Click] Edit Membership -> Uncheck from each Deployment Package
Examples
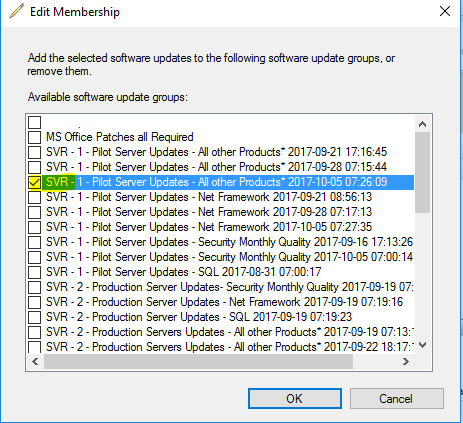
Figure 14 Removing Expired Updates From SUG
Software Update Groups Cleanup
Overview
Once an Update Group has been automatically created, used and replaced by a new Update Group of the same exact type, the old group can safely be deleted. This helps keep the environment clean and remove unnecessary Software Update Group deployments.
Procuedure
- Within the SCCM Console go to Software Library\Overview\Software Updates\Software Update Groups
- Sort by Name
- Delete the older of identical Software Update Groups if no longer user
Examples
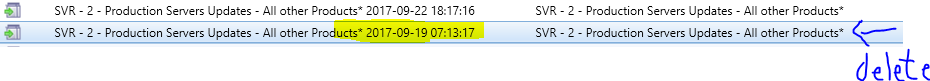
Figure 15 Deleting Old Software Update Groups
-
View Active Deployments


Leave a Reply
Want to join the discussion?Feel free to contribute!