Intune Guide – Overview
Microsoft Intune
By dmaiolo 2018-03-14
This article is part of a six-part series I have put together on Microsoft Intune.
- History of Microsoft Intune
- Intune Overview
- Mobile Device Management (MDM)
- Conditional Access
- Policies
- Mobile Application Management (MAM)
Intune Overview

Enterprise Mobility + Security (EMS)

Microsoft’s flagship mobility management product is called Enterprise Mobility + Security (EMS) suite. Intune can be purchased as a stand-alone subscription or as part of EMS, which acts as a single license to use:
- Intune: Device and App Management: Manage and protect apps and data across multiple devices
- Azure Active Directory Premium: Identity & Access Management: Manage identities across On-Premises and cloud. Single sign on and self-service for any application.
- Azure Rights Management Services: Information Protection: Encryption, identity and authorization protects files and email
- Advanced Threat Analytics: Behavior based threat analytics: Identify suspicious activities and advanced threats.
The core Enterprise Mobility Management (EMM) functionality of EMS is provided by Intune, responsible for Mobile Device Management (MDM), Mobile Application Management (MAM) and a separate level of PC management separate from SCCM (driven from the cloud).
Enterprise Mobility Management (EMM)
Enterprise Mobility Management (EMM) is a term that describes the process of managing mobile devices, wireless networks, and other mobile computing services in an enterprise environment. As enterprises integrate more smartphone and tablet devices into the workplace, EMM has become increasingly significant. From an EMS perspective, Intune is the EMM.
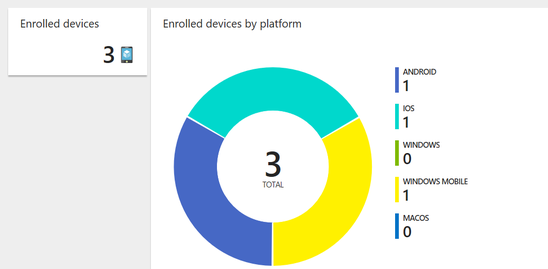
Mobile Device Management (MDM) Intune
Mobile device management (MDM) is a term for the administration of mobile devices, such as smartphones, tablet computers, laptops and desktop computers. Intune can manage both corporate devices and a “bring your own device” (BYOD). MDM allows you to control management, inventory, app deployment, provisioning, and retirement.
Mobile Application Management (MAM) Intune
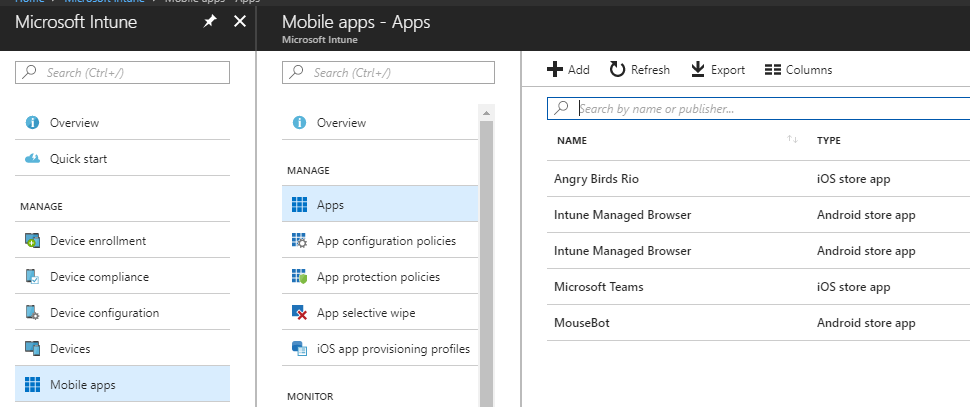
Mobile application management (MAM) envelops the services responsible for provisioning and controlling access to mobile apps used in an enterprise settings on corporate owned devices and BYOD..
Intune leverages MAM to set App Protection Policies at the app level for use with or without MDM device enrollment. Intune’s MAM helps protect corporate data with the policies that restrict data outflow such as Copy, Paste, Save As, provide encryption at rest, enforce application access and compliance, and remove corporate data at the application level.
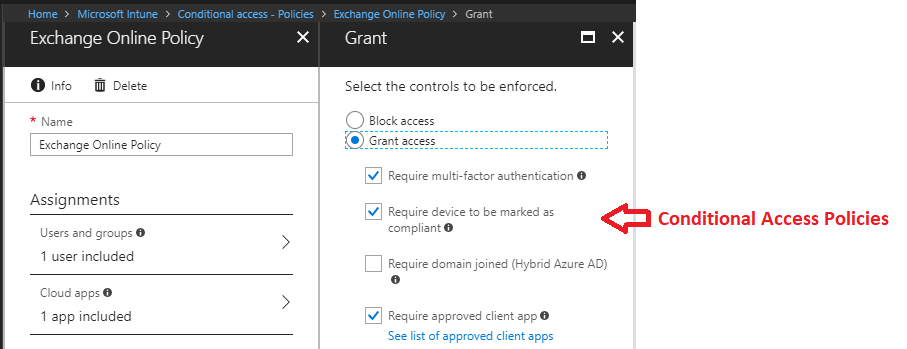
Conditional Access Intune
Intune allows you to manage access to corporate data by ensuring that only managed and compliant devices, aka “Healthy” devices, are able to access corporate email and files. If the device is not managed by Intune or compliant with IT policies (such as password strength, encryption, OS version), the access is blocked.
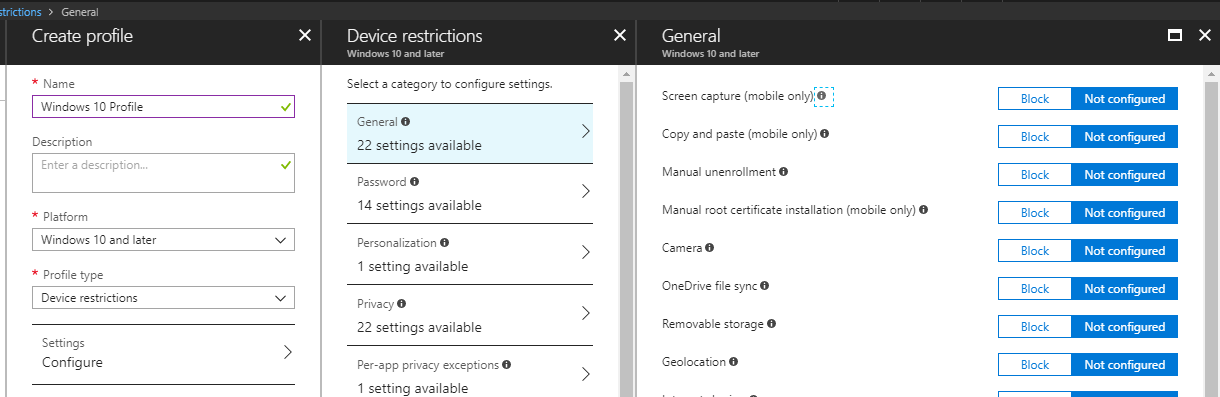
PC Management Intune
In addition to managing mobile devices, Intune also manages Windows 10 computers using the Intune agent or via MDM. Intune also works with System Center Configuration Manager to support more advanced PC and server management scenarios.
Mobile Content Management (MCM)
A Mobile Content Management system (MCMs) stores and delivers content and services to mobile devices, such as ringtones, games, text-messaging and news in the business-2-consumer market. From Microsoft’s vantage point, this service is handled by Microsoft OneDrive.
Mobile Information Management (MIM)
Mobile information management (MIM) is a generic security strategy that involves keeping sensitive data encrypted and allowing only approved applications to access or transmit it. From Microsoft’s vantage point, this service is handled by Microsoft OneDrive
Identity

Intune leverages its identity component through Azure Active Directory (AD) with options for the directory source to be cloud only or to sync to On-Premises. Azure AD provides the area to store all of the users that are used within Intune. In other words, any users in Intune are actually just users in Azure AD.
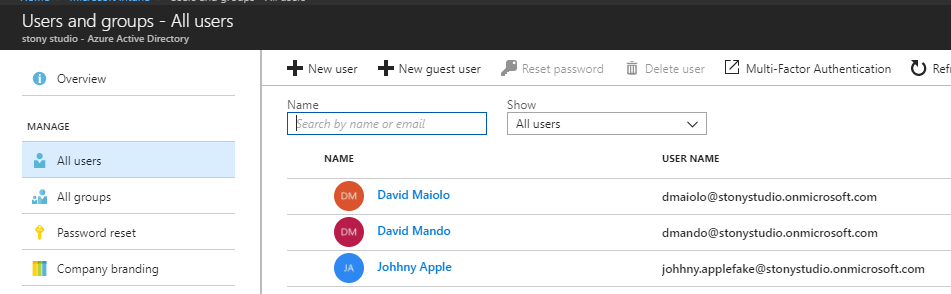
If you already use and have users within Azure AD with Office 365, Intune can leverage the same Azure AD database so that you do not have to recreate it.
Hybrid Integration

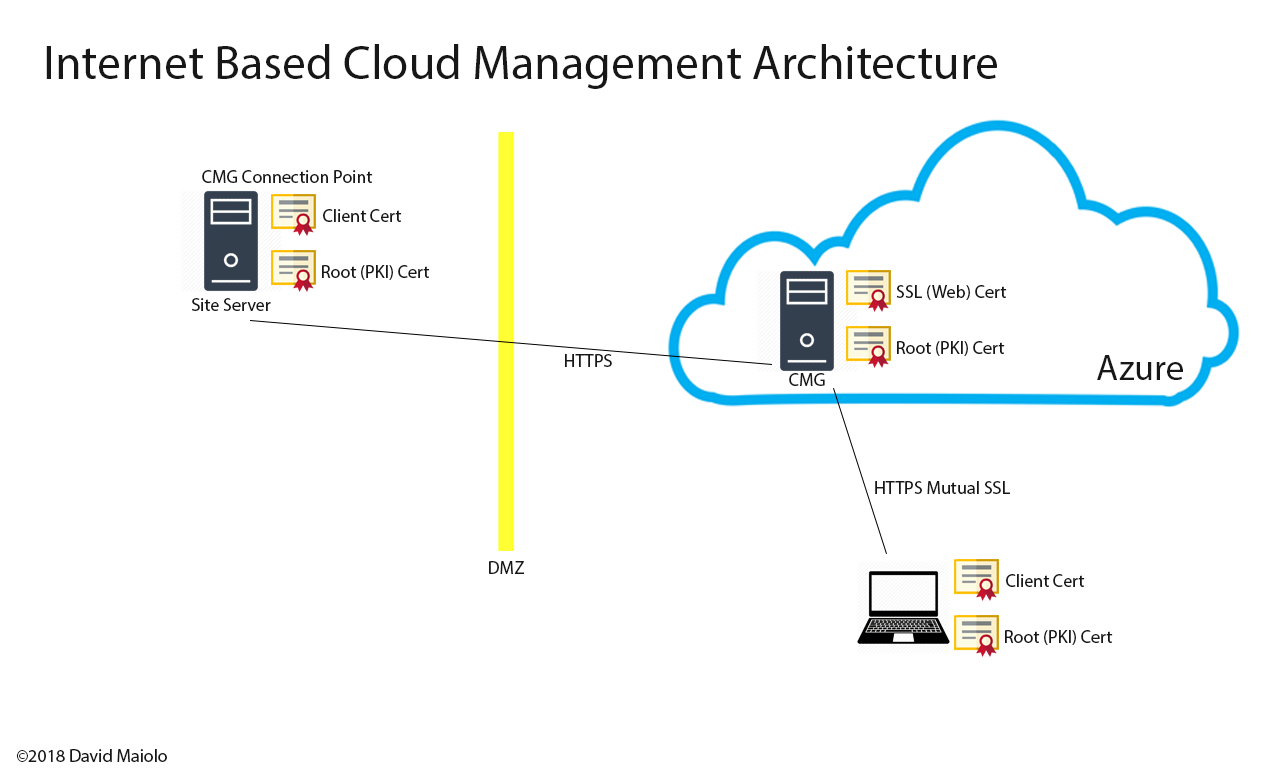
The first thing to think of when setting up Intune is who should be the MDM authority: Intune, SCCM or Intune + SCCM (co-management). Once the MDM authority is set, Intune is hard configured in that mode and reversing to a different mode requires a support call into Microsoft.
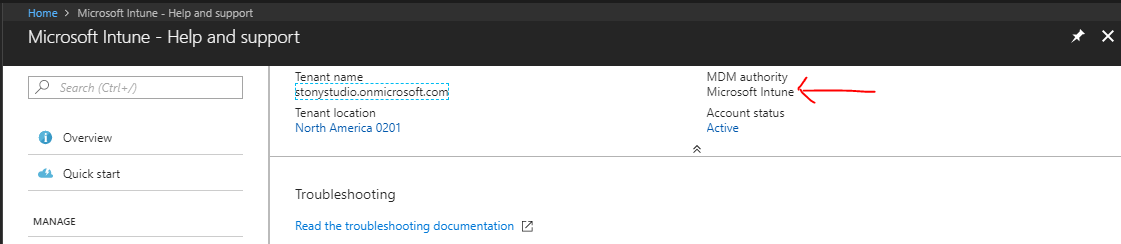
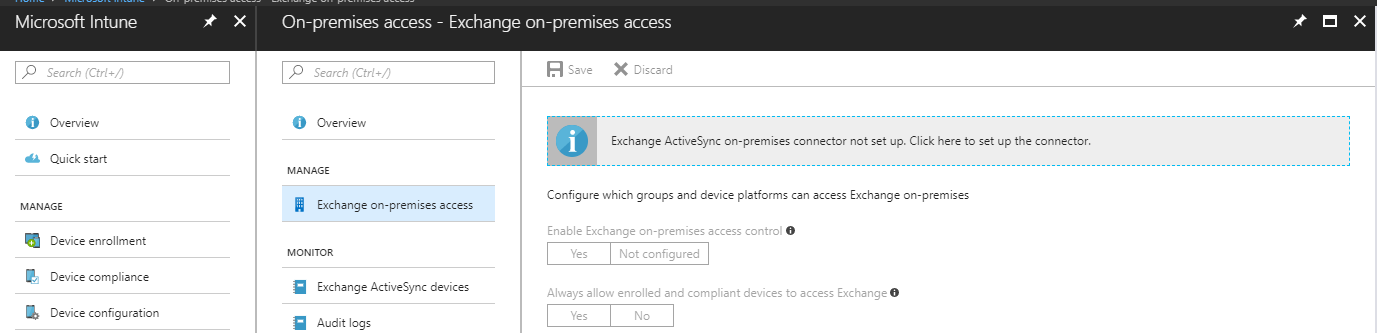
On-Premises Connectors

The most popular On-Premises connector is the Microsoft Exchange Connector, which uses Conditional Access to make sure the device is compliance before a device can access email. The on-premises Exchange connector is also responsible for discovering mobile devices that connect to on-premises Exchange Servers by synchronizing the existing Exchange Active Sync (EAS) record with Intune.
Another popular On-Premises connector is the Microsoft Intune Certificate Connector which is used to configure your infrastructure, then create and assign Simple Certificate Enrollment Protocol (SCEP) certificate profiles with Intune
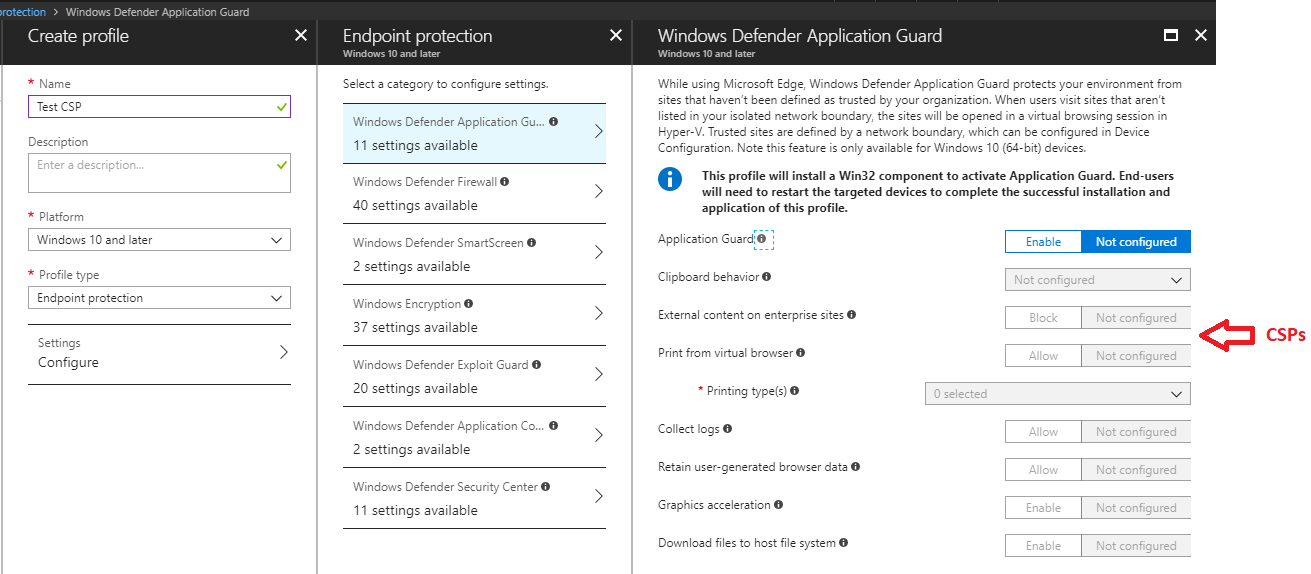
Device Applicability (Configuration Service Providers)

One of the things you’ll notice when configuring policies within Intune is that not every policy supports every device. Configuration service providers (CSPs) expose device configuration settings in Windows 10 and determine what is possible to manage on the device.
A CSP is an interface in Windows 10 between configuration settings specified in a provisioning document and configuration settings on the device. They function similar to Group Policy in that they provide an interface to read, set, modify, or delete configuration settings for a given feature. Typically, these settings map to registry keys, files or permissions, where some are configurable and some are read-only.
User Roles

Role Bases Administration Control (RBAC) is built right into Azure AD and Intune and provides different roles available to manage things within the Intune tenant.
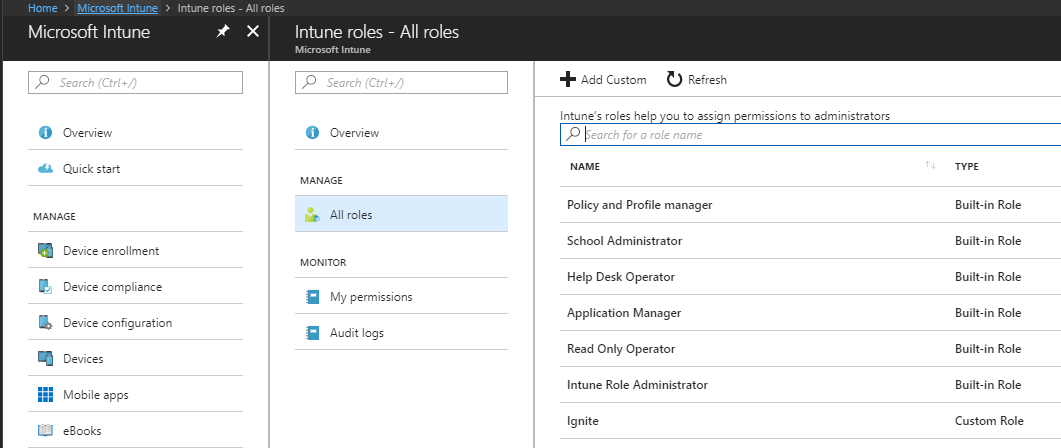
Role Definitions
Role definition: The name of a role, the resources it manages, and the permissions granted for each resource.
Members: The user groups that are granted the permissions.
Scope: The user or device groups that the members can manage.
Assignment: When the definition, members, and scope have been configured, the role is assigned.
Built-In Roles (from Azure AD)
Global Administrator: Access to all administrative features in Azure AD, as well as services that federate to Azure AD like Exchange Online, SharePoint Online, and Skype for Business Online.
Intune Service Administrator: Global permissions within, manage users, devices, and create and manage Intune groups.
Conditional Access Administrator: Only have permissions to view, create, modify, and delete conditional access policies.
Built-In Roles (Native to Intune)
Help Desk Operator: Performs remote tasks on users and devices, and can assign applications or policies to users or devices.
Policy and Profile Manager: Manages compliance policy, configuration profiles, Apple enrollment, and corporate device identifiers.
Read Only Operator: Views user, device, enrollment, configuration, and application information. Cannot make changes to Intune.
Application Manager: Manages mobile and managed applications, and can read device information.
School Administrator: Manages Windows 10 devices in Intune for Education.
Special Permissions
When the Device Enrollment Administrator permission is added to an Intune Role, members of that role can enroll more than the 5 device maximum.
Licensing Devices for Intune (Enabling Use)
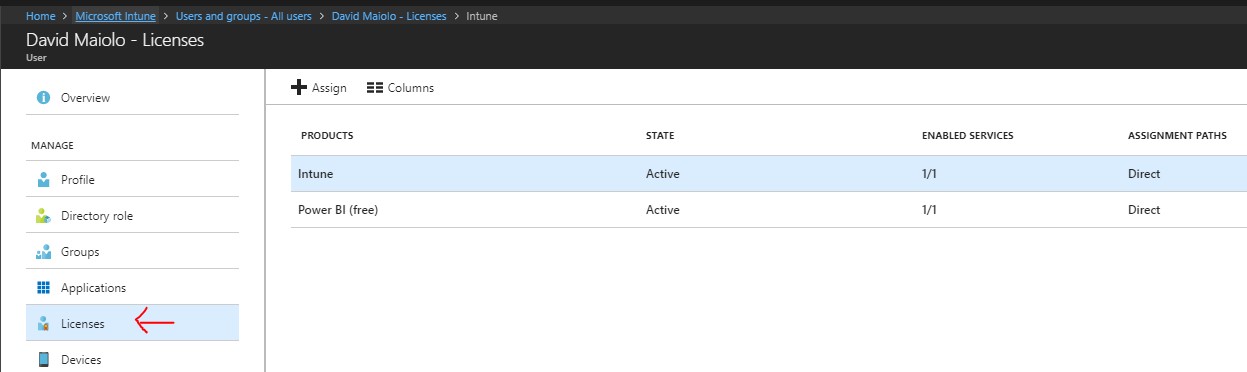
Users must be enabled for device enrollment before they can begin enrolling devices into Intune. In Intune Standalone you can enable users individually (or with PowerShell) and with Hybrid Configuration Manager you select a collection for enrollment.

The purpose of requiring you to enable each user is to give you the granularity to control who can and cannot enroll devices as a large enterprise environment might have thousands of users.


Leave a Reply
Want to join the discussion?Feel free to contribute!