Embracing Digital Transformation: Insights and Tips
Digital transformation is a critical journey every business must undertake to stay relevant and competitive in today’s rapidly changing technological landscape. As someone who has navigated the complexities of modern technology through my work at DBGM Consulting, Inc., I’ve seen firsthand the transformative impact of integrating digital processes. Drawing on the wisdom of industry experts like Aaron Shapiro, former CEO of HUGE, let’s delve into how businesses can embrace digital transformation effectively.
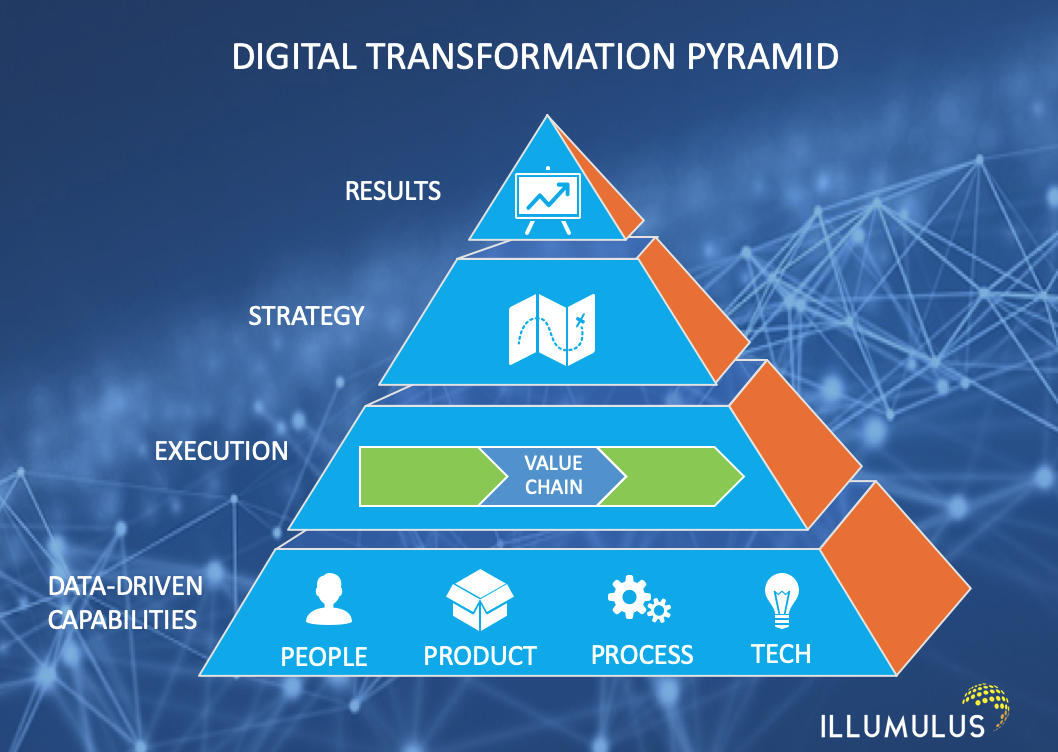
The Benefits of Digital Transformation
Digital transformation holds the key to unlocking unprecedented efficiencies, enhancing customer engagement, and streamlining operations. In my experience, the transition towards digital is not just a luxury but a necessity. It fuels innovation and offers businesses a competitive edge in the ever-evolving market landscape.
Streamlined Operations
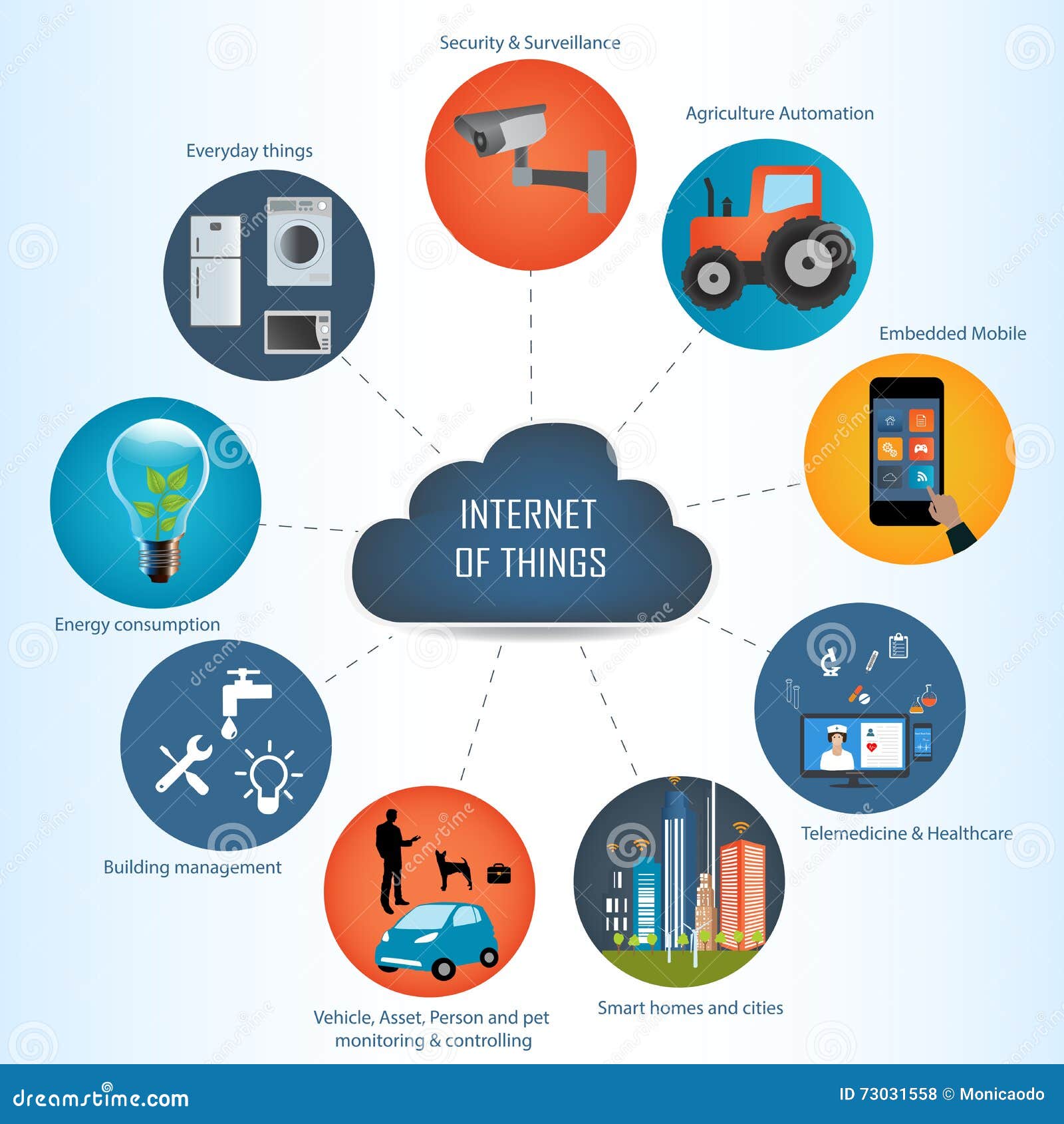
One of the most immediate benefits of digital transformation is the streamlining of operations. Through my work in AI and cloud solutions, I’ve aided businesses in automating mundane tasks and optimizing workflows, thereby significantly reducing operational costs and improving efficiency.
Enhanced Customer Engagement
Moreover, the digital realm opens up innovative channels for customer engagement. Utilizing chatbots and personalized marketing strategies, companies can provide bespoke customer experiences, fostering loyalty and driving sales.
Starting Your Digital Transformation Journey
Embarking on digital transformation doesn’t have to be a daunting task. With strategic planning and the right mindset, businesses can step into the digital age without incurring outrageous costs.
Identify Your Digital Goals
Understanding your business’s specific needs and objectives is the first step toward a successful digital transformation. Whether it’s enhancing customer experience, streamlining operations, or improving security measures, setting clear goals is crucial.
Leverage Affordable Cloud Solutions
Cloud technology plays a pivotal role in digital transformation. In my journey, from working on IT projects with AWS to helping clients with cloud migration strategies, I’ve seen how cloud solutions facilitate scalability, flexibility, and innovation at a fraction of traditional costs.
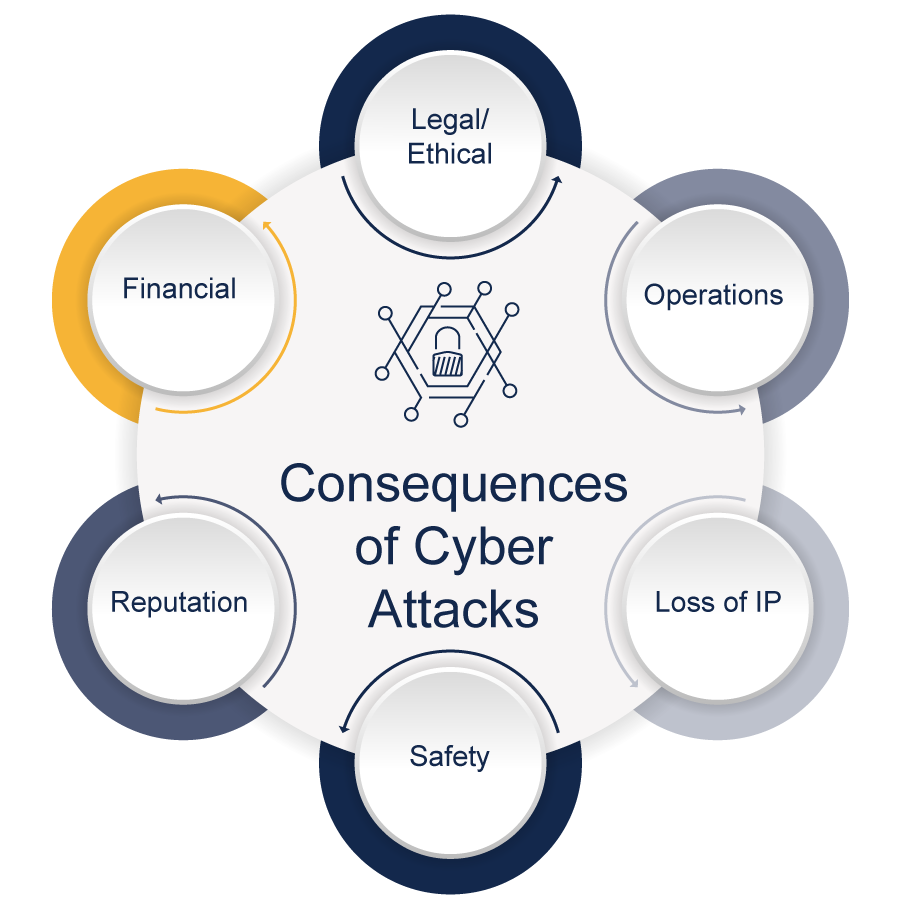
Focus on Security and Compliance
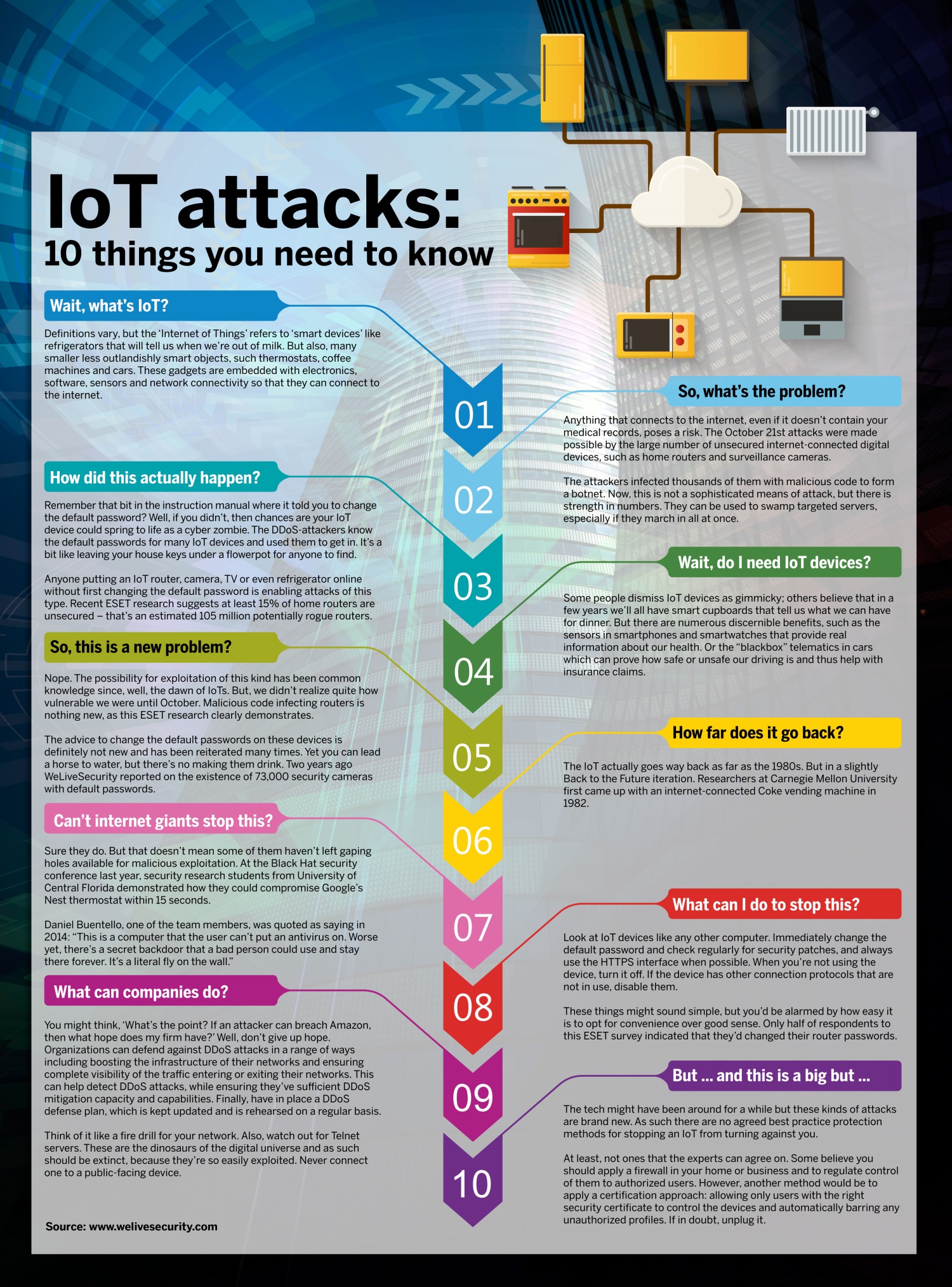
As businesses digitize their operations, the importance of cybersecurity and regulatory compliance cannot be overstated. Implementing robust security measures and ensuring compliance safeguard your business against digital threats and legal repercussions.
The Road Ahead
Digital transformation is an ongoing process, not a one-time project. It requires continuous adaptation and learning. As someone deeply invested in the future of technology, I remain optimistic about the possibilities that AI and digital innovation hold for our society.
However, it’s crucial to approach this journey with caution, understanding the implications of technology on privacy, ethics, and social interaction. I advocate for a balanced approach, leveraging technology to enhance human capabilities without overshadowing the human touch.
Conclusion
Transforming your business digitally is an essential step towards staying relevant in the fast-paced digital era. Drawing from personal experiences and the insights of industry veterans like Aaron Shapiro, it’s clear that with the right strategies and mindset, digital transformation can lead to substantial business growth and innovation.
Embracing this change requires identifying your specific goals, taking advantage of cloud technologies, and prioritizing security and compliance. As we navigate this digital journey, let’s remain diligent, innovative, and thoughtful about the impact of technology on our world.

Focus Keyphrase: Digital Transformation
 >
> >
> >
> >
> >
> >
> >
>



 >
> >
> >
> >
> >
> >
>