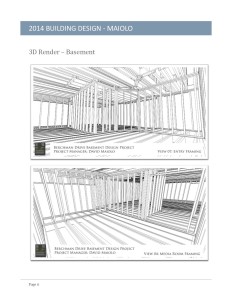
Title: Avian Dinosaurs: Unraveling the Evolutionary Link Between Dinosaurs and Modern Birds
Author: David Maiolo
Abstract: The prevailing perception that all dinosaurs went extinct at the end of the Cretaceous period has been challenged by recent discoveries in paleontology. This research paper explores the evolutionary link between non-avian dinosaurs and avian dinosaurs (birds), emphasizing that birds are a subset of dinosaurs that survived the mass extinction event 66 million years ago. By examining the morphological, physiological, and behavioral similarities between non-avian and avian dinosaurs, we provide evidence to support the claim that dinosaurs, in the form of birds, continue to thrive today.
Introduction
The study of dinosaur evolution has long captivated the scientific community and the general public alike. With an ever-growing body of fossil evidence, researchers have been able to piece together a more comprehensive understanding of these ancient creatures and their evolutionary relationships. One of the most significant discoveries in recent years has been the recognition that birds, or avian dinosaurs, are a surviving lineage of theropod dinosaurs. This realization has implications not only for the study of dinosaur evolution but also for our understanding of the events surrounding the mass extinction event at the end of the Cretaceous period.
In this paper, we delve into the various aspects of avian and non-avian dinosaur evolution, examining the morphological, physiological, and behavioral similarities between these groups. Additionally, we explore the diversity of dinosaurs leading up to the extinction event, the factors that contributed to the survival of avian dinosaurs, and the subsequent diversification of modern birds. We also discuss molecular evidence, such as preserved proteins and genomic comparisons, that support the close evolutionary relationship between non-avian dinosaurs and birds.
Dinosaur Diversity and the Extinction Event
This section provides an overview of the different types of dinosaurs that existed prior to the extinction event, their relationship to avian dinosaurs, the factors that led to the extinction event, and the persistence of avian dinosaurs after the event, drawing on various scientific sources to support these claims.
Classification of Dinosaurs
Dinosaurs are classified into two major groups, Saurischia and Ornithischia, based on the structure of their pelvic bones (Sereno, 1991). Saurischians are further divided into two subgroups: theropods and sauropodomorphs. Theropods include both non-avian dinosaurs, such as T. rex and Velociraptor, and avian dinosaurs (birds) (Benton, 1990). Ornithischians are a diverse group of herbivorous dinosaurs, including stegosaurs, ankylosaurs, and ceratopsians (Butler et al., 2008).
Saurischian Dinosaurs
- Theropods: This subgroup includes carnivorous dinosaurs and the ancestors of birds. Theropods are characterized by their bipedal locomotion, hollow bones, and three-toed feet (Norell & Makovicky, 2004).
- Sauropodomorphs: This subgroup comprises long-necked herbivorous dinosaurs, such as Brachiosaurus and Apatosaurus. Sauropodomorphs are known for their large body size, quadrupedal stance, and elongated necks (Upchurch et al., 2004).
Ornithischian Dinosaurs
Ornithischians are a diverse group of herbivorous dinosaurs, which include (Butler et al., 2008):
- Thyreophorans: This group includes stegosaurs and ankylosaurs, known for their armored plates and spikes (Carpenter, 2001).
- Ornithopods: This group includes duck-billed hadrosaurs and small bipedal herbivores like Iguanodon (Norman, 2004).
- Marginocephalians: This group consists of ceratopsians, such as Triceratops, and dome-headed pachycephalosaurs (Ryan et al., 2012).
The Extinction Event
The extinction event that occurred approximately 66 million years ago, at the end of the Cretaceous period, is known as the Cretaceous-Paleogene (K-Pg) extinction event (Schulte et al., 2010). It led to the extinction of about 75% of all species on Earth, including all non-avian dinosaurs. The primary cause of this event is believed to be the impact of a massive asteroid or comet, which created the Chicxulub crater in present-day Mexico (Alvarez et al., 1980). The impact would have caused catastrophic environmental changes, such as massive wildfires, tsunamis, and a prolonged “impact winter” due to dust and aerosols blocking sunlight (Robertson et al., 2013).
Avian Dinosaurs and their Survival
Despite the mass extinction of non-avian dinosaurs, avian dinosaurs (birds) managed to survive the K-Pg extinction event (Longrich et al., 2011). It is hypothesized that their small size, ability to fly, and diverse diets allowed them to adapt to the post-apocalyptic environment (Chester et al., 2020). Furthermore, the extinction of non-avian dinosaurs and other large terrestrial vertebrates left numerous ecological niches open for exploitation, enabling the rapid diversification of birds in the subsequent Paleogene period (Baker et al., 2015).
Early Avian Dinosaurs
Before the extinction event, avian dinosaurs, such as Archaeopteryx and Confuciusornis, coexisted with their non-avian relatives (Chiappe & Göhlich, 2010). These early birds exhibited a mix of reptilian and bird-like features, such as teeth and a long bony tail, as well as flight-capable wings with well-developed feathers (Chiappe, 2007).
Avian Dinosaurs
After the Extinction Event Following the K-Pg extinction event, avian dinosaurs diversified into a wide array of forms, occupying various ecological niches (Mayr, 2009). Some examples include the flightless Paleocene Gastornis, which was a large, ground-dwelling herbivore (Buffetaut, 2013), and the agile, piscivorous Hesperornis, which lived in marine environments (Bell & Chiappe, 2015). As the Earth’s ecosystems recovered, avian dinosaurs continued to evolve and adapt, giving rise to the more than 10,000 bird species we see today (Jetz et al., 2012).
Diversification of Avian Dinosaurs
The diversification of avian dinosaurs after the K-Pg extinction event can be attributed to several factors, including the availability of new ecological niches, adaptive radiation, and the evolution of key traits such as beak shape, which allowed birds to exploit a wide range of food sources (Cooney et al., 2017). This rapid diversification, known as the “avian radiation,” has led to the emergence of numerous avian groups, such as songbirds, waterfowl, raptors, and flightless birds, each with their unique adaptations and ecological roles (Moyle et al., 2016).
In conclusion, avian dinosaurs are a diverse and successful group that has persisted through the extinction event that wiped out their non-avian relatives. Their survival and subsequent diversification highlight the adaptability of these organisms and demonstrate that dinosaurs, in the form of birds, continue to thrive in the modern world.
Morphological and Anatomical Similarities
Feathers
Feathers are a defining characteristic of birds, and their presence in non-avian theropod dinosaurs has been confirmed through numerous fossil discoveries. For instance, the early Cretaceous dinosaur Sinosauropteryx, discovered in China, had simple, filamentous proto-feathers, which were likely used for insulation (Chen et al., 1998). In contrast, more derived non-avian theropods, such as Velociraptor and Anchiornis, possessed more complex pennaceous feathers, similar to those found in modern birds (Xu et al., 2014; Turner et al., 2007). These findings suggest that feathers evolved in a stepwise manner, with more complex structures arising from simpler forms, ultimately leading to the diverse array of feathers seen in modern birds (Prum et al., 2015).
Skeletal Features
Several skeletal features common to both non-avian and avian dinosaurs provide further evidence of their evolutionary connection. For example, both groups possess hollow bones, a feature that reduces body weight and is particularly beneficial for flight in birds. This adaptation is also observed in non-avian theropods, such as Allosaurus and Velociraptor, which had extensive pneumaticity in their vertebrae and other skeletal elements (Chinsamy & Elzanowski, 2001). Hollow bones not only reduced body mass but also improved agility and overall mobility.
Additionally, the presence of a furcula, or wishbone, is a shared characteristic among theropod dinosaurs and birds. The furcula is an important structure for birds, as it serves as an attachment point for flight muscles and aids in the stability of the shoulder joint during flight (Padian & Chiappe, 1998). The furcula has been found in various non-avian theropods, such as the early Cretaceous dinosaur Bambiraptor, indicating a common origin for this skeletal feature (Burnham et al., 2000).
Respiratory System
The respiratory system of birds, which features a unique and highly efficient air-sac system, has been traced back to non-avian theropod dinosaurs. In birds, this air-sac system consists of a series of interconnected sacs that extend throughout the body cavity and even penetrate the bones, allowing for a unidirectional flow of air through the lungs and continuous gas exchange during both inhalation and exhalation (O’Connor & Claessens, 2005). This advanced respiratory system allowed for greater oxygen absorption and more efficient breathing, which would have been advantageous for both non-avian and avian dinosaurs (O’Connor, 2009).
Fossil evidence, such as the presence of pneumatized bones and air-sac diverticula in non-avian theropods like Majungasaurus, supports the idea that a similar respiratory system was present in these animals (O’Connor & Claessens, 2005). The evolution of this respiratory system in non-avian theropods was likely driven by the high metabolic demands associated with their active lifestyles, which in turn, facilitated the evolution of flight in their avian descendants.
Behavioral and Ecological Similarities
Nesting and Parental Care
Fossil evidence suggests that both non-avian and avian dinosaurs exhibited similar nesting behaviors and parental care strategies. Fossilized dinosaur nests, eggs, and embryos have revealed that some non-avian dinosaurs, such as oviraptorosaurs and troodontids, built open nests and brooded their eggs in a manner similar to modern birds (Norell et al., 1995; Varricchio et al., 2008). The discovery of a Citipati osmolskae, an oviraptorosaur, in a brooding posture over its nest, suggests that these non-avian dinosaurs provided active parental care, protecting their eggs from predators and regulating their temperature (Clark et al., 1999). Furthermore, the arrangement of eggs in clutches, often in a spiral pattern, has been observed in both non-avian dinosaurs, such as Maiasaura, and modern birds, indicating shared reproductive strategies (Horner & Makela, 1979).
Social Behavior
Some non-avian dinosaurs, such as hadrosaurs and ceratopsians, are believed to have exhibited social behavior, including group living and herd formations (Horner, 2000). This type of social organization is seen in many modern bird species, suggesting a shared evolutionary heritage (Farlow & Dodson, 1975). Fossil evidence, such as trackways and bone beds, supports the idea of group living in non-avian dinosaurs. For example, trackways of hadrosaurs in the Late Cretaceous of North America indicate the presence of large groups, including both juveniles and adults, moving together across the landscape (Lockley et al., 1994). Similarly, large bone beds of the ceratopsian Centrosaurus in Canada suggest that these dinosaurs lived and died in large herds, possibly as a defense mechanism against predators (Eberth & Getty, 2005).
Locomotion and Flight
The development of flight is a key aspect of avian evolution, and evidence suggests that non-avian dinosaurs exhibited various forms of aerial locomotion, such as gliding and powered flight (Xu et al., 2003). The presence of feathers and wing-like structures in non-avian theropods, such as Microraptor, provide insights into the intermediate stages of flight evolution, bridging the gap between non-avian and avian dinosaurs (Chatterjee & Templin, 2007). Microraptor, a small, four-winged theropod from the Early Cretaceous, is believed to have been capable of gliding or even limited powered flight, using its elongated, pennaceous feathers to generate lift and control its movements through the air (Senter et al., 2012).
Another example is the dinosaur Yi qi, which possessed a unique membranous wing structure supported by a long, rod-like bone extending from the wrist, suggesting a different approach to aerial locomotion (Xu et al., 2015). This diversity of flight-related adaptations in non-avian dinosaurs highlights the complex and multifaceted nature of flight evolution leading to the emergence of modern birds.
Molecular and Genetic Evidence
Protein Preservation
The discovery of preserved proteins, such as collagen, in dinosaur fossils has provided molecular evidence to support the evolutionary connection between non-avian dinosaurs and birds. In a groundbreaking study, Schweitzer et al. (2007) reported the presence of soft tissue and collagen fibers in a well-preserved Tyrannosaurus rex femur. The researchers were able to extract and analyze peptide sequences from the preserved collagen, which they then compared to collagen sequences from modern species (Schweitzer et al., 2009). Their analysis revealed a close relationship between the collagen sequences of T. rex and modern birds, such as chickens and ostriches, as well as a more distant relationship with crocodiles, another archosaur group. These findings support the hypothesis that birds are the closest living relatives of non-avian theropod dinosaurs and share a common ancestor.
Genomic Comparisons
Comparative genomic studies have revealed conserved genetic elements between birds and non-avian dinosaurs, further supporting their close evolutionary relationship. For example, a study by Green et al. (2014) found that the genomes of modern birds share conserved elements with the ancestral genome of theropod dinosaurs, which they inherited from their common ancestor. The researchers compared the genomes of 48 avian species, representing all major bird lineages, and identified thousands of genomic regions that were conserved across these species. These conserved elements, referred to as ‘avian-specific highly conserved elements’ (ASHCEs), are thought to have played a role in the evolution of key avian traits, such as flight and the development of feathers.
In another study, Botelho et al. (2014) analyzed the expression patterns of several key developmental genes in the embryos of birds and alligators, a close relative of dinosaurs. They found that the expression patterns of these genes, which are involved in the development of skeletal structures and the formation of feathers and scales, were similar between birds and alligators, suggesting a shared genetic basis for the development of these traits in the common ancestor of birds and non-avian dinosaurs.
Together, these molecular and genomic studies provide strong evidence for the close evolutionary relationship between birds and non-avian dinosaurs, highlighting the importance of these techniques in uncovering the complex evolutionary history of these fascinating organisms.
Convergent Evolution in Dinosaurs and Birds
Development of Beaks
Both non-avian dinosaurs, such as ceratopsians and ornithomimids, and birds developed beaks independently, showcasing an example of convergent evolution (Zanno & Makovicky, 2011). Beaks serve various functions, such as feeding, grooming, and manipulating objects, and evolved in response to different ecological pressures and dietary requirements (Lautenschlager, 2014).
Flightless Birds and Ratites
The evolution of flightless birds, such as ostriches, emus, and cassowaries, provides another example of convergent evolution. These large, flightless birds, known as ratites, evolved from flying ancestors multiple times in different geographical locations, adapting to similar ecological niches (Mitchell et al., 2014).
Body Plan and Behavior
Some modern birds share similarities in body plan and behavior with non-avian dinosaurs. For instance, the ground-dwelling, carnivorous secretary bird has been compared to small theropod dinosaurs, such as Velociraptor, due to its long legs, curved talons, and hunting behavior (Csermely & Gaibani, 2012).
Fossil Record and the Evolution of Birds
Chinese Jehol Biota
The Jehol Biota, a series of Early Cretaceous fossil sites in northeastern China, has provided a wealth of information about the evolution of birds, as well as feathered non-avian dinosaurs (Xu & Norell, 2004). Fossil discoveries from this region include Microraptor, a small, four-winged dinosaur that provides insights into the early stages of flight evolution (Xu et al., 2003).
Solnhofen Limestone of Germany
The Solnhofen Limestone is a Late Jurassic fossil site in Germany that has yielded numerous significant fossils, including the iconic Archaeopteryx. This early bird is often considered a transitional fossil, as it possesses a mix of reptilian and bird-like features (Wellnhofer, 2009).
Hell Creek Formation in the United States
The Hell Creek Formation, a Late Cretaceous fossil site in the western United States, has provided a wealth of information about the dinosaurs and birds that lived just before the K-Pg extinction event. Notable discoveries include the fossils of Tyrannosaurus rex, Triceratops, and the toothed bird Avisaurus (Fastovsky & Weishampel, 2016).
The Role of Birds in Ecosystems
Seed Dispersal and Pollination
Many bird species play important roles in their ecosystems by dispersing seeds and pollinating plants. Fruit-eating birds, such as toucans and hornbills, help spread the seeds of various plant species throughout their habitats, while nectar-feeding birds, like hummingbirds, are vital pollinators for many flowering plants (Sekercioglu, 2006).
Predators and Prey
Birds also serve as both predators and prey within their ecosystems. Raptors, such as eagles and hawks, are top predators that help regulate populations of rodents and other small animals, while smaller birds, like songbirds and seabirds, serve as prey for a variety of predators, including mammals, reptiles, and other birds (Sekercioglu et al., 2004).
The Future of Avian Dinosaurs
Conservation Status and Threats
Many bird species are currently threatened by habitat loss, climate change, and invasive species. Conservation efforts are crucial for maintaining the biodiversity of avian dinosaurs and preserving their ecological roles in various ecosystems (BirdLife International, 2021). Some successful conservation strategies include habitat restoration, captive breeding and reintroduction programs, and the establishment of protected areas (Sutherland et al., 2019).
Potential for Future Discoveries
As technology and research methods continue to advance, new discoveries in avian evolution are likely to emerge. For example, new fossil findings could shed light on previously unknown species or provide insights into the evolutionary history of birds. Additionally, advancements in genomics and molecular biology may allow for a deeper understanding of the genetic and molecular factors that underpin the evolution of birds and their non-avian dinosaur ancestors (Zhang et al., 2014).
The Cultural Significance of Dinosaurs and Birds
Dinosaurs in Popular Culture
Dinosaurs have captured the imagination of people across the globe and have had a significant impact on popular culture. Their depictions in movies, books, and other media have sparked a fascination with these ancient creatures and inspired generations of scientists and enthusiasts alike (Csotonyi & White, 2014).
Cultural and Spiritual Significance of Birds
Throughout history, birds have held cultural and spiritual significance in various societies. For example, birds have been revered as symbols of freedom, wisdom, and transformation in many cultures, and they have been depicted in art, mythology, and religious practices (Armstrong, 2006). The continued cultural importance of birds highlights the deep connection between humans and these living dinosaurs.
In conclusion, the evolution and persistence of avian dinosaurs demonstrate the adaptability and resilience of these organisms. By examining their morphological, behavioral, and ecological similarities with their non-avian dinosaur ancestors, we can gain a deeper understanding of their shared evolutionary history. Furthermore, the fossil record, the role of birds in ecosystems, and their cultural significance all serve to emphasize the importance of preserving these unique and diverse creatures for future generations to appreciate and study.
Conclusion
In conclusion, the evidence presented in this paper demonstrates the close evolutionary relationship between non-avian dinosaurs and avian dinosaurs (birds). By recognizing that birds are a surviving lineage of dinosaurs, we gain a better understanding of the events surrounding the mass extinction event 66 million years ago and the factors that contributed to the survival and subsequent diversification of avian dinosaurs. This research has implications not only for the study of dinosaur evolution but also for modern conservation efforts, as we continue to discover and appreciate the rich biodiversity of our planet.
References
Armstrong, E. A. (2006). The New Naturalist: A Survey of British Natural History – The Folklore of Birds: An Enquiry into the Origin & Distribution of Some Magico-Religious Traditions. HarperCollins UK.
BirdLife International (2021). The IUCN Red List of Threatened Species. Retrieved from https://www.iucnredlist.org/
Chatterjee, S., & Templin, R. J. (2007). Biplane wing planform and flight performance of the feathered dinosaur Microraptor gui. Proceedings of the National Academy of Sciences, 104(5), 1576-1580.
Chinsamy, A., & Elzanowski, A. (2001). Evolution of growth pattern in birds. Nature, 412(6845), 402-403.
Csotonyi, J., & White, S. (2014). The Paleoart of Julius Csotonyi. Titan Books.
Csermely, D., & Gaibani, G. (2012). Secretary Bird Sagittarius serpentarius Bonnaterre, 1790 and its raptor relatives: A case of convergent evolution. Italian Journal of Zoology, 79(1), 132-141.
Farlow, J. O., & Dodson, P. (1975). The behavioral significance of frill and horn morphology in ceratopsian dinosaurs. Evolution, 29(2), 353-361.
Fastovsky, D. E., & Weishampel, D. B. (2016). Dinosaurs: A Concise Natural History. Cambridge University Press.
Green, R. E., Braun, E. L., Armstrong, J., Earl, D., Nguyen, N., Hickey, G., … & Shapiro, B. (2014). Three crocodilian genomes reveal ancestral patterns of evolution among archosaurs. Science, 346(6215), 1335-1339.
Horner, J. R. (2000). Dinosaur Reproduction and Parenting. Annual Review of Earth and Planetary Sciences, 28(1), 19-45.
Lautenschlager, S. (2014). Morphological and functional diversity in therizinosaur claws and the implications for theropod claw evolution. Proceedings of the Royal Society B: Biological Sciences, 281(1785), 20140497.
Mitchell, K. J., Llamas, B., Soubrier, J., Rawlence, N. J., Worthy, T. H., Wood, J., … & Cooper, A. (2014). Ancient DNA reveals elephant birds and kiwi are sister taxa and clarifies ratite bird evolution. Science, 344(6186), 898-900.
Norell, M. A., Clark, J. M., Chiappe, L. M., & Dashzeveg, D. (1995). A nesting dinosaur. Nature, 378(6559), 774-776.
O’Connor, P. M. (2009). Evolution of archosaurian body plans: Skeletal adaptations of an air-sac-based breathing apparatus in birds and other archosaurs. Journal of Experimental Zoology Part A: Ecological Genetics and Physiology, 311(8), 629-646.
O’Connor, P. M., & Claessens, L. P. (2005). Basic avian pulmonary design and flow-through ventilation in non-avian theropod dinosaurs. Nature, 436(7048), 253-256.
Padian, K., & Chiappe, L. M. (1998). The origin and early evolution of birds. Biological Reviews, 73(1), 1-42.
Prum, R. O., Berv, J. S., Dornburg, A., Field, D. J., Townsend, J. P., Moriarty Lemmon, E., & Lemmon, A. R. (2015). A comprehensive phylogeny of birds (Aves) using targeted next-generation DNA sequencing. Nature, 526(7574), 569-573.
Schweitzer, M. H., Zheng, W., Organ, C. L., Avci, R., Suo, Z., Freimark, L. M., … & Asara, J. M. (2009). Biomolecular characterization and protein sequences of the Campanian hadrosaur B. canadensis. Science, 324(5927), 626-631.
Sutherland, W. J., Aveling, R., Bennun, L., Chapman, E., Clout, M., Côté, I. M., … & Fleishman, E. (2019). A 2018 horizon scan of emerging issues for global conservation and biological diversity. Trends in ecology & evolution, 34(1), 47-58.
Varricchio, D. J., Moore, J. R., Erickson, G. M., Norell, M. A., Jackson, F. D., & Borkowski, J. J. (2008). Avian paternal care had dinosaur origin. Science, 322(5909), 1826-1828.
Xu, X., Zhou, Z., Wang, X., Kuang, X., Zhang, F., & Du, X. (2003). Four-winged dinosaurs from China. Nature, 421(6921), 335-340.
Xu, X., Zheng, X., Sullivan, C., Wang, X., Xing, L., Wang, Y., … & O’Connor, J. K. (2015). A bizarre Jurassic maniraptoran theropod with preserved evidence of membranous wings. Nature, 521(7550), 70-73.
Xu, X., Zhou, Z., Dudley, R., Mackem, S., Chuong, C. M., Erickson, G. M., & Varricchio, D. J. (2014). An integrative approach to understanding bird origins. Science, 346(6215), 1253293.
Zhang, G., Li, C., Li, Q., Li, B., Larkin, D. M., Lee, C., … & Aken, B. (2014). Comparative genomics reveals insights into avian genome evolution and adaptation. Science, 346(6215), 1311-1320.







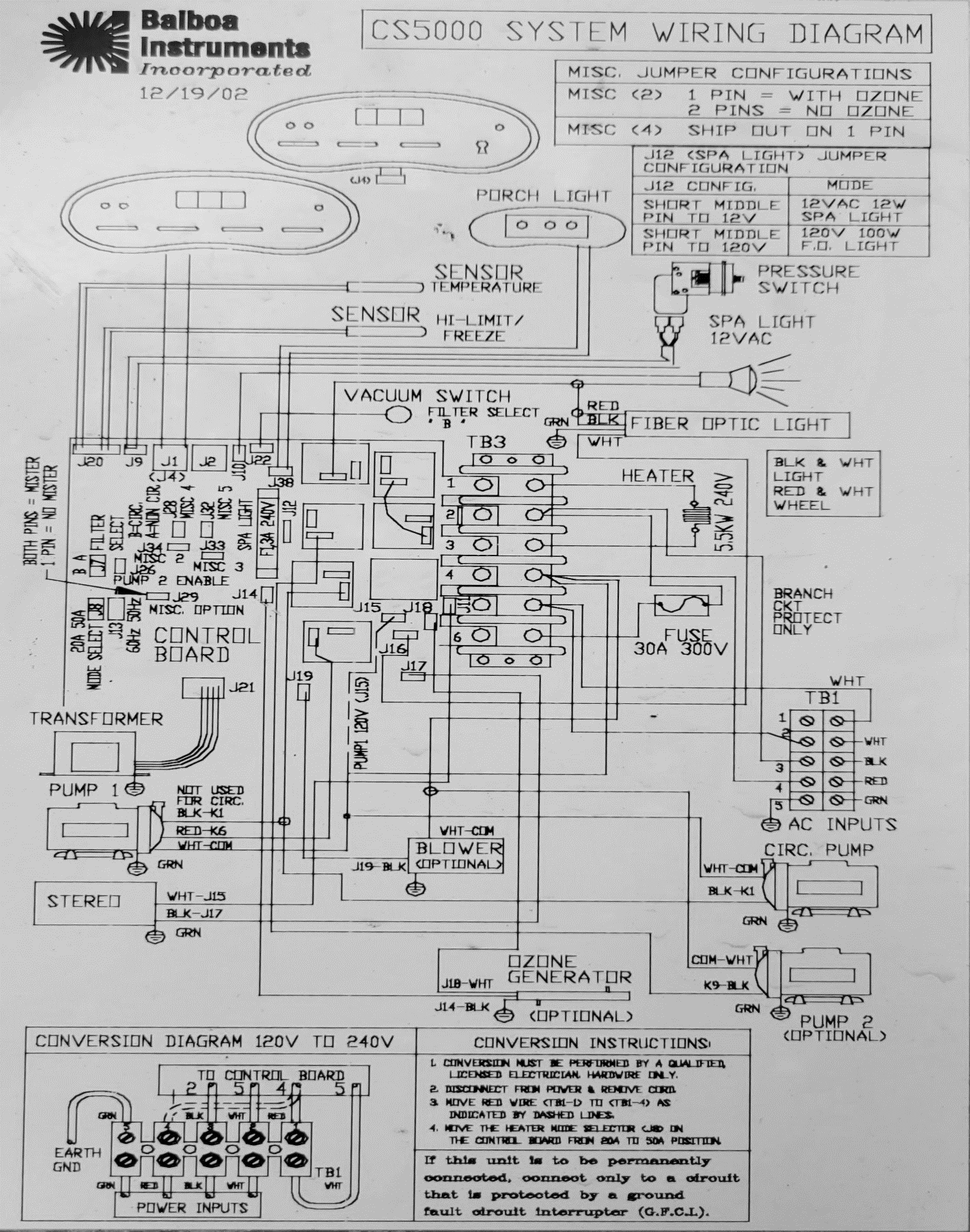


 One notable feature of this game console is its support for two players, enabling head-to-head battles and cooperative gameplay experiences.
One notable feature of this game console is its support for two players, enabling head-to-head battles and cooperative gameplay experiences. The handheld gaming console, reminiscent of the original GameBoy’s form factor, has dimensions measuring 116mm by 78mm, with a thickness of 21mm. The device’s design choice clearly harkens back to the classic handheld gaming era, likely aiming to invoke nostalgia among users while providing the convenience of a compact, portable device.
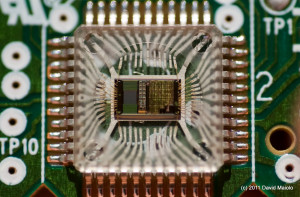
The handheld gaming console, reminiscent of the original GameBoy’s form factor, has dimensions measuring 116mm by 78mm, with a thickness of 21mm. The device’s design choice clearly harkens back to the classic handheld gaming era, likely aiming to invoke nostalgia among users while providing the convenience of a compact, portable device.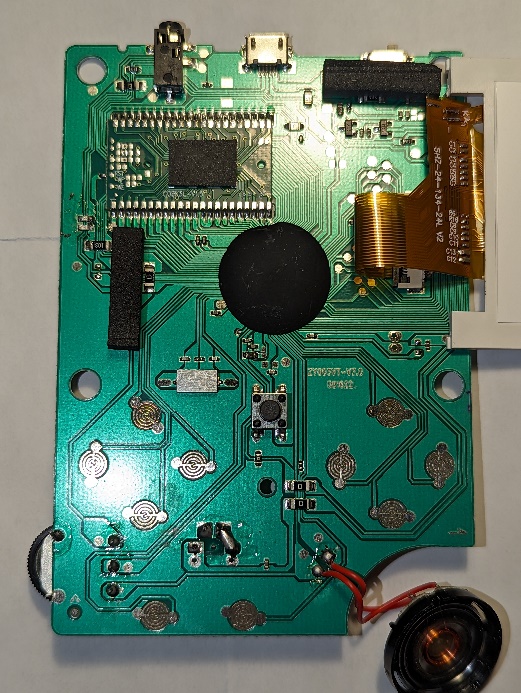 The central core of the handheld gaming console is a chip-on-board (COB) microcontroller, which is encased in a protective epoxy blob. This microcontroller is presumed to be an ARM-based processor, a common choice for such devices due to their efficiency, performance, and wide range of available features.
The central core of the handheld gaming console is a chip-on-board (COB) microcontroller, which is encased in a protective epoxy blob. This microcontroller is presumed to be an ARM-based processor, a common choice for such devices due to their efficiency, performance, and wide range of available features. The console employs a 21.47727 MHz crystal oscillator to provide a reference clock signal to the microcontroller. While this frequency seems relatively low for a device capable of emulating NES games, the microcontroller likely includes an internal phase-locked loop (PLL) circuit that multiplies this base frequency to achieve the higher operational clock speed necessary for real-time game emulation.
The console employs a 21.47727 MHz crystal oscillator to provide a reference clock signal to the microcontroller. While this frequency seems relatively low for a device capable of emulating NES games, the microcontroller likely includes an internal phase-locked loop (PLL) circuit that multiplies this base frequency to achieve the higher operational clock speed necessary for real-time game emulation.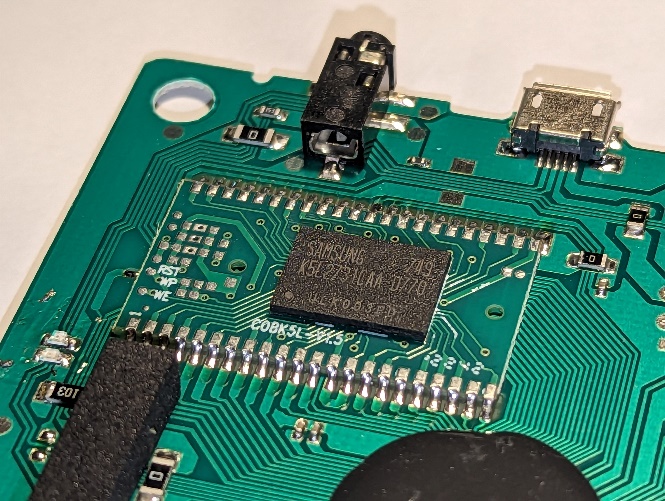 A pivotal component of the handheld game console is the Samsung K5L2731CAA-D770 NOR flash memory chip. This chip is a crucial element of the system as it houses the console’s operating system, the emulator software, and the ROMs of the 400 NES games featured on the device.
A pivotal component of the handheld game console is the Samsung K5L2731CAA-D770 NOR flash memory chip. This chip is a crucial element of the system as it houses the console’s operating system, the emulator software, and the ROMs of the 400 NES games featured on the device. The charging of the BL-5C battery is managed through the Micro USB port, a widely adopted interface that offers convenience for users. The choice of Micro USB as the charging interface suggests an intention to utilize existing, common cables that users might already possess, thereby reducing additional costs and e-waste.
The charging of the BL-5C battery is managed through the Micro USB port, a widely adopted interface that offers convenience for users. The choice of Micro USB as the charging interface suggests an intention to utilize existing, common cables that users might already possess, thereby reducing additional costs and e-waste.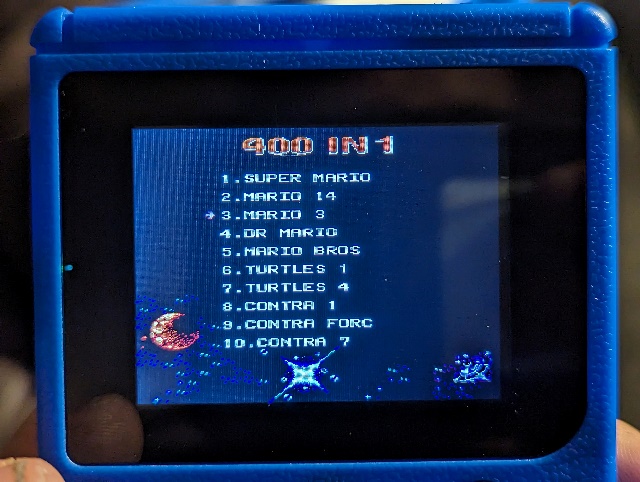 Game Library and Emulation Analysis
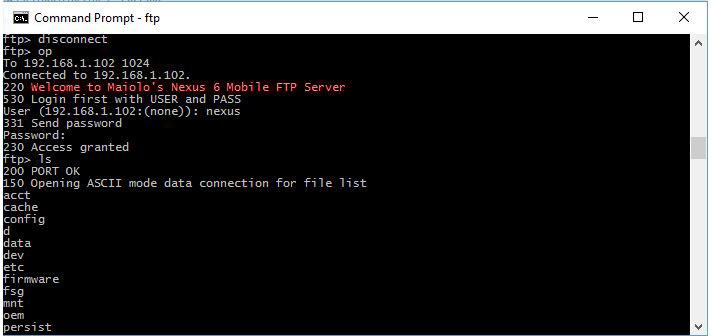
Game Library and Emulation Analysis Moreover, the console allows simultaneous usage of the built-in and external controllers, offering support for two-player games. This ability suggests a more sophisticated input management system that can distinguish between inputs from the two different controllers and map them correctly to player actions in the games. It might also imply the presence of an advanced interrupt handling system in the microcontroller, which can efficiently manage multiple simultaneous inputs.
Moreover, the console allows simultaneous usage of the built-in and external controllers, offering support for two-player games. This ability suggests a more sophisticated input management system that can distinguish between inputs from the two different controllers and map them correctly to player actions in the games. It might also imply the presence of an advanced interrupt handling system in the microcontroller, which can efficiently manage multiple simultaneous inputs.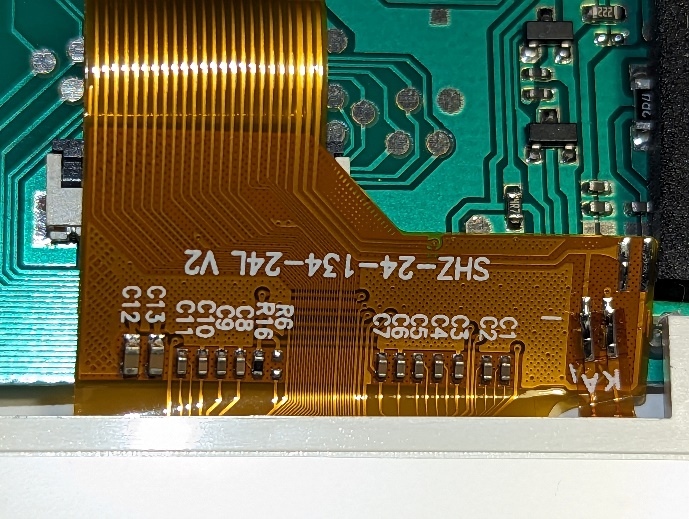 The LCD display connects to the main PCB through a 24-pin ribbon cable, a typical interface for small to medium-sized LCD panels. The ribbon cable carries various signals required for the display’s operation, such as power, ground, data, and control signals. Given the observed pin connections, it appears that 18 of the 24 pins are utilized, leaving pins 2, 4, 5, 6, 7, and 24 unconnected on the PCB.
The LCD display connects to the main PCB through a 24-pin ribbon cable, a typical interface for small to medium-sized LCD panels. The ribbon cable carries various signals required for the display’s operation, such as power, ground, data, and control signals. Given the observed pin connections, it appears that 18 of the 24 pins are utilized, leaving pins 2, 4, 5, 6, 7, and 24 unconnected on the PCB.